Quick Answer / CLI Summary: If you need the configuration immediately, use these commands in your MikroTik terminal: (Read below for the full step-by-step guide and firewall security setup) One of the main issues with consumer internet connections is that they rarely provide static IPs by default. If your ISP assigns dynamic IPs via DHCP …
Networking
This is where I talk about the traditional networking, and protocols and its workings simplified with packet captures and others.
Quick Answer / CLI Template (HQ Side) If you are an experienced engineer and just need the syntax for your specific topology, here is the complete CLI block for the HQ Firewall. (Scroll down for the detailed explanation, Policy configuration, and Branch-side steps) Introduction We have set up IPsec site-to-site VPNs using the FortiGate Web GUI …
If you’re new to MikroTik routers and eager to explore its functionality, the best way to learn is by using real hardware. However, investing in a router right away might not be ideal, and you’d prefer to test things out in a lab environment. So, what can you do? A great solution is to use …
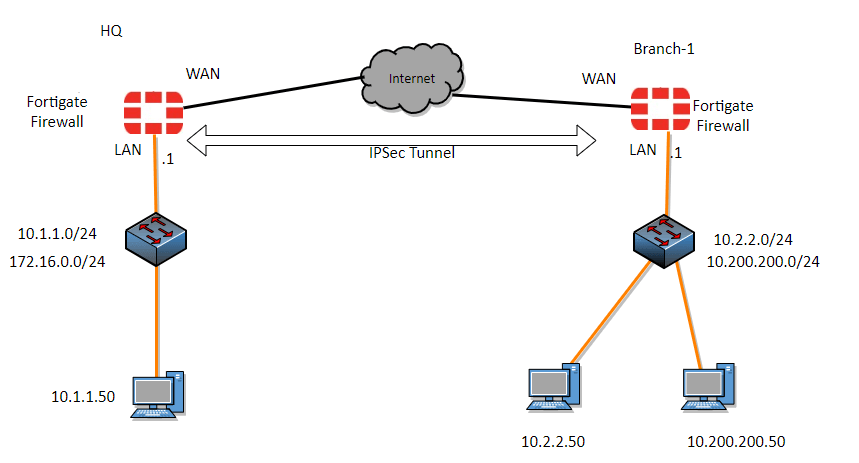
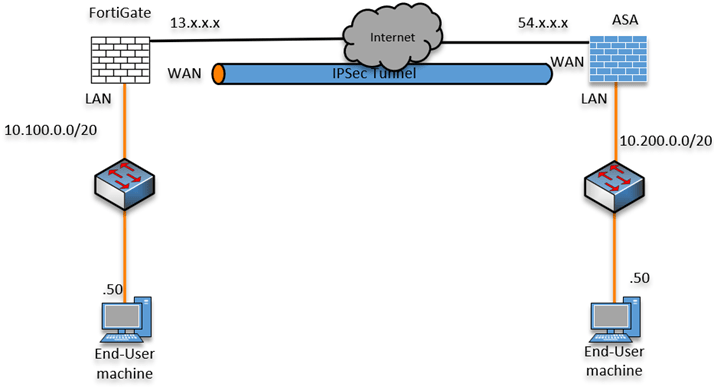
We have looked at how you can set up an IPsec VPN between two FortiGate firewalls in our last blog article, and it works great. But sometimes you will have multiple subnets that you would want to route through the FortiGate firewall, so how do you route multiple subnets across the IPsec tunnel using the …
We have set up IPsec in one of our previous articles, and some readers reached out to me and said, yes the tunnel came up and I can initiate communication towards the other side, but what if I have multiple subnets how do I enable the communication to both sides? So, in this blog article …
You’ve got a brand new MikroTik router and now you’re wondering how to set up IPsec between your headquarter’s FortiGate firewall and this new MikroTik router. For those of you new to MikroTik, it might feel somewhat overwhelming to understand its functionality, especially when you’re trying to configure the IPsec site-to-site VPN between the FortiGate …
When it comes to MikroTik, you can pretty much run everything out of the box using the Quickset option. However, sometimes you may want to override the initial basic configuration manually. So, in this blog article, we will start configuring MikroTik from scratch. You might be thinking where do I begin with the basic configurations, …
Quick Answer / CLI Summary: If you prefer the terminal, paste this command to create the PPPoE interface immediately: (Read below for the full WinBox guide, including VLAN tagging and troubleshooting) When connecting a MikroTik router to an ISP, you generally have two options: DHCP (Plug & Play) or PPPoE (Username & Password). While DHCP …
We have setup MikroTik in different environments, its time for us to build IPsec tunnel between two sites where we have MikroTik routers. What is the IPsec tunnel in MikroTik ? An IPsec tunnel in MikroTik refers to a secure communication channel established between two remote sites or networks using the IPsec (Internet Protocol Security) …
The MikroTik router has gained popularity in recent times for home and small business branch deployments due to its support for firewall features and IPsec compatibility. One of the key advantages of this hardware is its affordability compared to other vendor products, which has contributed to its growing popularity. Another advantage of the MikroTik router …
If you have just acquired a MikroTik router and you’re unfamiliar with it, this blog article will guide you on getting started. Feeling a bit overwhelmed is completely normal when dealing with a new MikroTik device, especially if it’s your first time setting it up for a small branch office. In this blog article, we’ll …
In the previous blog post, we discussed how to set up different user permissions in pfSense. Now, we’re going to take it a step further and configure pfSense to communicate with the RADIUS server. This configuration allows for user authentication into the pfSense dashboard. If you’re planning to use OpenVPN on pfSense, you can use …
When introducing a pfSense firewall into your environment, you initially have complete control over the firewall by default. However, when granting access to the operations team, you need to implement different levels of permissions. This ensures that L1 engineers cannot inadvertently shut down critical components on the pfSense firewall. Unlike Cisco, where you can utilize …
The other day, I was trying to set up a radius client to talk to the NPS server in windows, and everytime when I try to authenticate against the windows NPS server, it fails. Finally I was able to find the issue, and it was related to the windows firewall blocking the radius request, hence …
When you deploy a cisco ios network infrastructure, we would set up the local account for the initial configuration, and later we would require some sort of centralised radius or tacacs + location that will help you authenticate the cisco devices. It is not ideal to use a local account, because, as in when the …
The Microsoft Active Directory (AD) is one of the most popular centralized domain controllers available today. In most enterprises, you will find Microsoft AD deployed as the primary system. Sometimes, you may want to manage your VPN or network infrastructure using the same centralized server to act as a RADIUS server. To accomplish this, you …
This is the continuation of the last blog article, where we have taken a look at how you can set up redundant IPsec tunnels between two palo alto firewalls with dual ISPs. So if you have not set up the IPsec tunnels yet, I would suggest you go back to the article here, and set …
You got a palo alto firewall at the edge of your branch network and the headquarters, and you are planning to run IPsec with a dynamic routing protocol on top of it. But you are confused with all the IPsec and BGP configurations, even if you get everything up and running how do you manage …
Palo Alto Networks is a leading provider of next-generation firewalls, and in my previous blog article, I have covered several topics related to the Palo Alto Firewall. In this article, I will provide a step-by-step guide on how to set up a basic DMZ configuration in the Palo Alto Firewall. By the end of this …
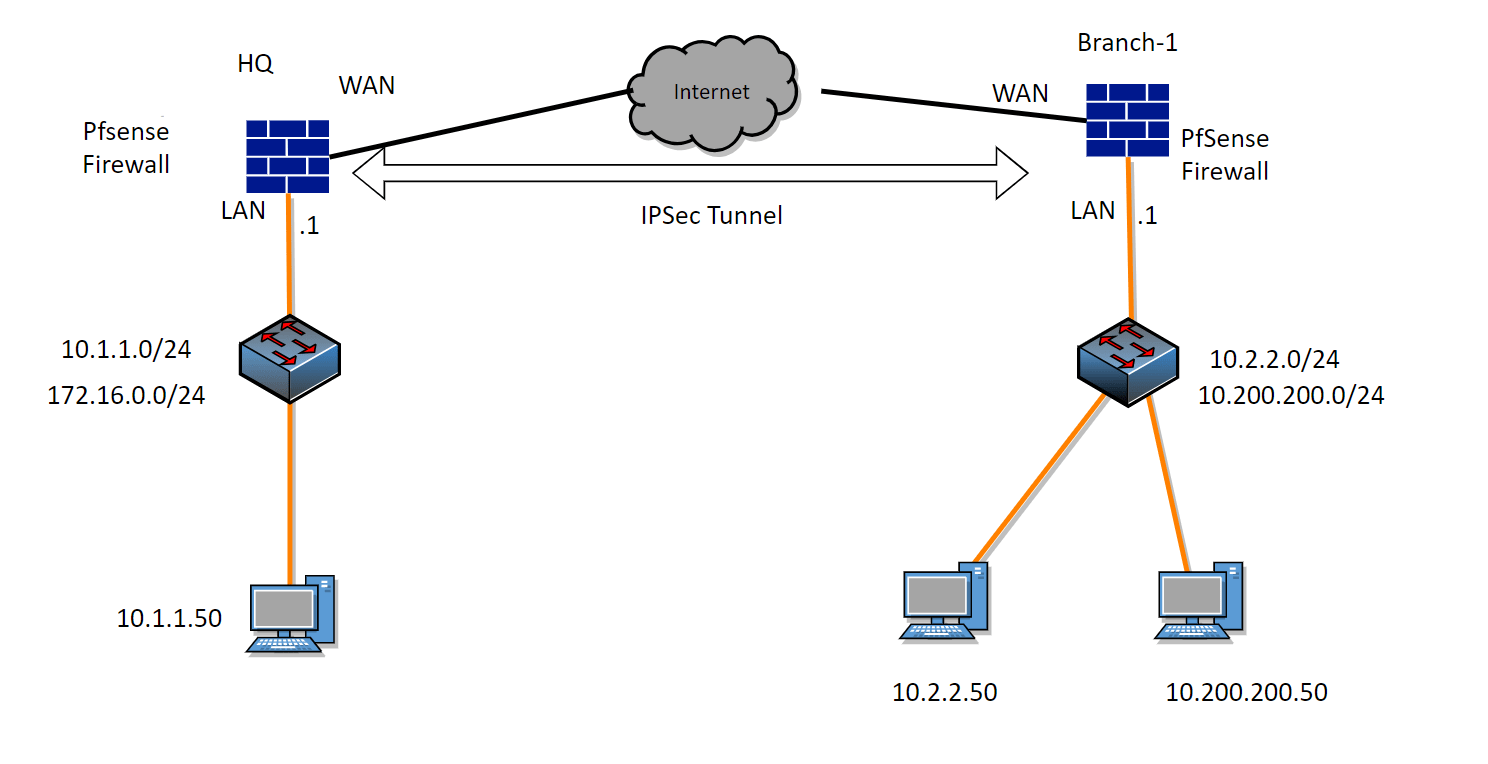
The pfSense firewall is a great open-source product that you can set up in your home network. If you would like to use it in an enterprise network, you can use a different version of the same product called pfSense Plus. Both products are identical, but the enterprise derivative receives the latest feature upgrades and …
The Sophos firewall is a powerful next-generation firewall commonly used by enterprise networks. As a network administrator or engineer, you may want to set up a test environment where you can make changes without impacting the production network. The best and cost-effective way to do this is by setting up a virtual lab. In this …
There are several firewall vendors, and Sophos is one of them, when it comes to network security. Many Enterprise customers utilize Sophos Firewall at the network’s edge, and it can also be used in a home lab. But not many of us have the resources to purchase expensive equipment and install it in our home …
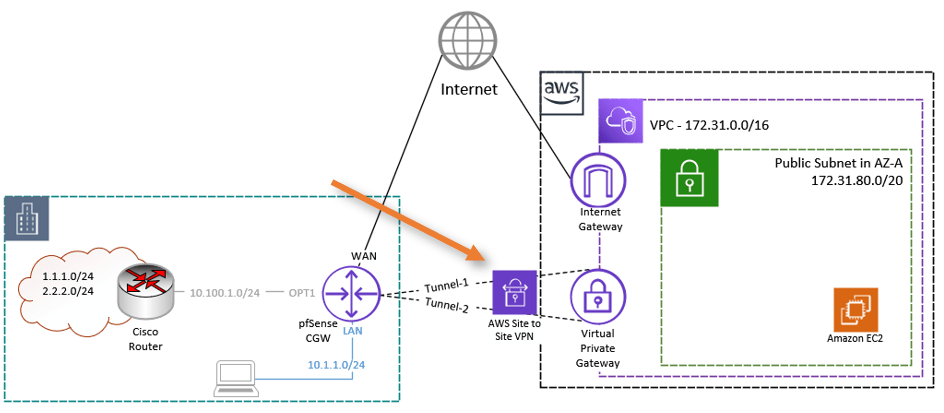
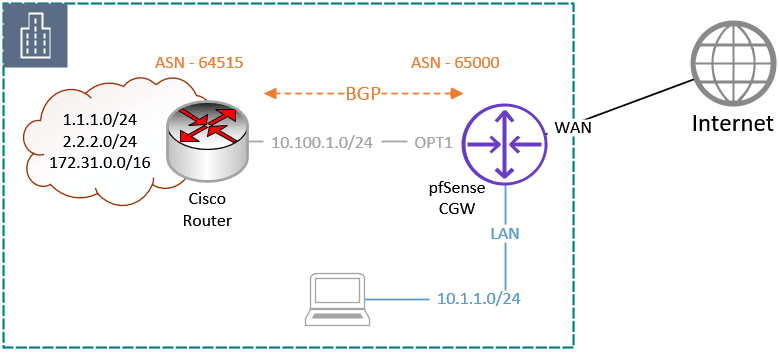
This is the continuation of the previous article, where we have set up two site-to-site tunnels from AWS to pfSense, as shown below. First being the primary and second being standby. Basically, we have built the transport over which you can now communicate with each side. However, to dynamically send and receive route advertisements and …
When you deploy the site-to-site VPN between AWS and pfSense using a static route, a phase1 will come up. However, the phase2 will remains down. As a result, the devices on both ends cannot communicate. Even if you try to connect phase 2 from Status->IPsec in pfsense manually, you will see the connection is not …
I’ve had pfSense running on my home network for a long time now. You might use it as your home network’s firewall because it is an excellent open-source firewall. However, you should utilize hardware from Netgate if you wish to integrate pfSense to an enterprise network. I have a PPPoE configured in my network to connect …
We use an IPsec site-to-site VPN tunnel to connect two sites. It provides security and is a lot cheaper than other means of connecting the WAN network. By default, most of the network will have internet access, and the devices they have at the edge of the network will have IPsec capability. That’s the only …
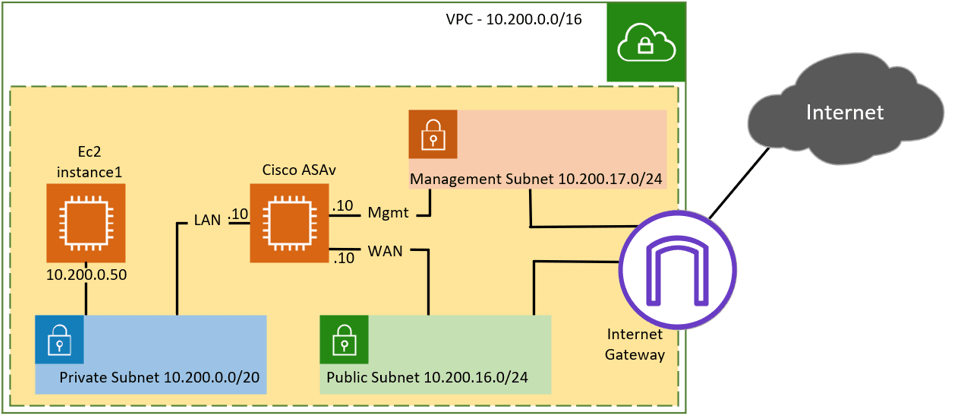
Asa is one of the popular firewall offerings from cisco, used by many on-prem enterprise networks. Many users are now using the ASAv on the AWS cloud; it sits at the edge of the cloud network protecting your AWS resources. You can also take advantage of this setup and configure end-user VPNs such as Any …
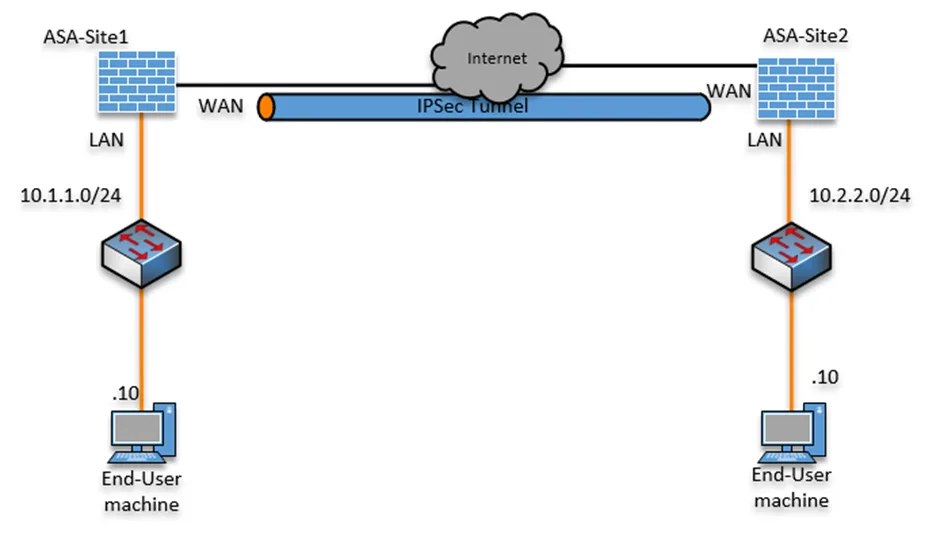
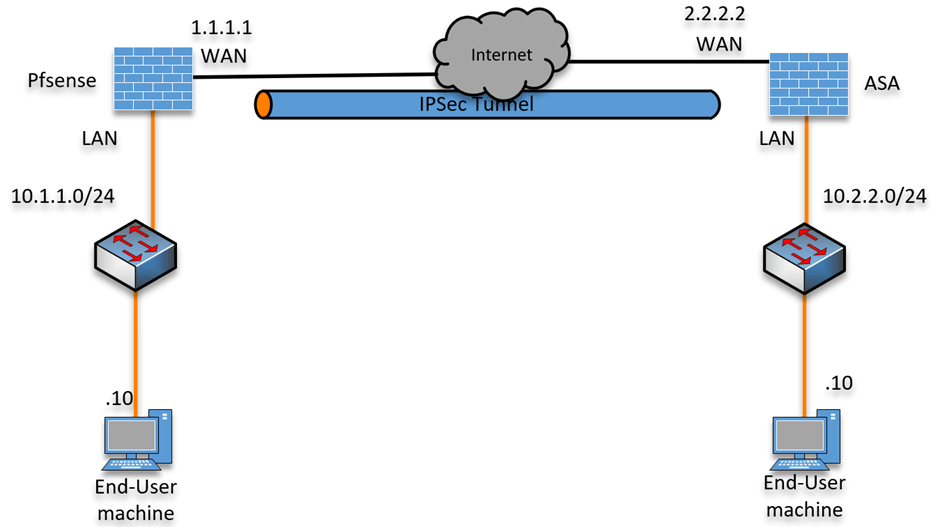
There are multiple ways to connect your inter offices using WAN. You can get MPLS, a Dedicated link. Those are the expensive ones, and there is SD-WAN. However, the cheapest and most popular method of connecting two different branch networks is using an IPsec site to site a VPN tunnel. If you have ASA on …
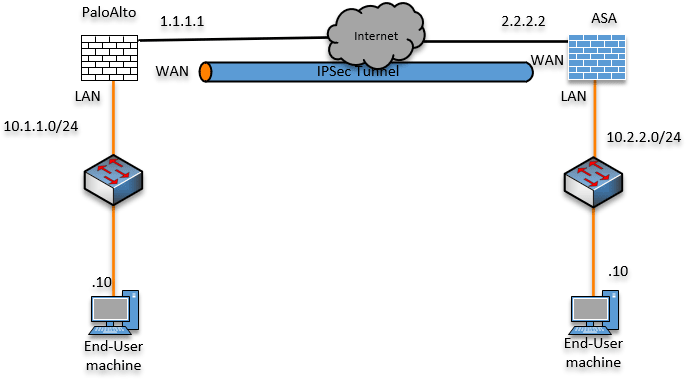
The Paloalto firewall is one of the popular next-generation firewalls in the market. I like Palolalto because it is very easy to use, especially for those who come from the Cisco world. The firewall offering from Cisco is the ASA – Adaptive security appliance. Though it provides security in your infrastructure, it lacks the features …
When you want to connect two remote sites, the easiest and cheapest way is to deploy an IPsec tunnel. The only requirement to connect both offices is that you need a device that supports IPsec capability and an internet connection. That’s it, and you can now build an IPsec tunnel successfully between two sites. ASA …