The pfSense firewall is a great open-source product that you can set up in your home network. If you would like to use it in an enterprise network, you can use a different version of the same product called pfSense Plus.
Both products are identical, but the enterprise derivative receives the latest feature upgrades and updates as they become available.
One of the advantages of using a pfSense firewall at the edge of your network is that you have full control over your network. You can set up OpenVPN as a client VPN, site-to-site VPNs, and one of the essential features of pfSense is port forwarding.
Port forwarding in pfSense forwards specific traffic from the internet to your LAN network that you have specified. For example, if you have an RDP server located in your home LAN network, you can access it remotely while you’re away, like while you’re in the office.
Is it safe to allow RDP port forwarding to LAN?
While it might seem like a convenient way to connect, it comes with inherent security risks that you should be aware of.
Port forwarding, if not done correctly, can create vulnerabilities in your network that hackers can exploit. It is crucial to take extra precautions and be vigilant while configuring port forwarding. Make sure to limit the source IP address and avoid leaving it open for anyone to access.
You should never keep the source IP as “any.” If you do so, someone else on the internet will be able to log in before you even get a chance to. So, if you follow the article mentioned here, you should be fine.
If possible, it is highly recommended to set up a VPN connection to access your devices remotely, as it provides an additional layer of security to your network.
Also, it is essential to use strong and unique passwords on the client-side to prevent unauthorized access.
From a firewall perspective, it is not recommended to have external-facing servers on your LAN network. It is best to set up a separate pfsense DMZ network for internet-facing sites and servers. This way, if your DMZ network is compromised, it will not affect your LAN network.
so with that, let’s go ahead and configure the pfsense RDP port forwarding in this blog.
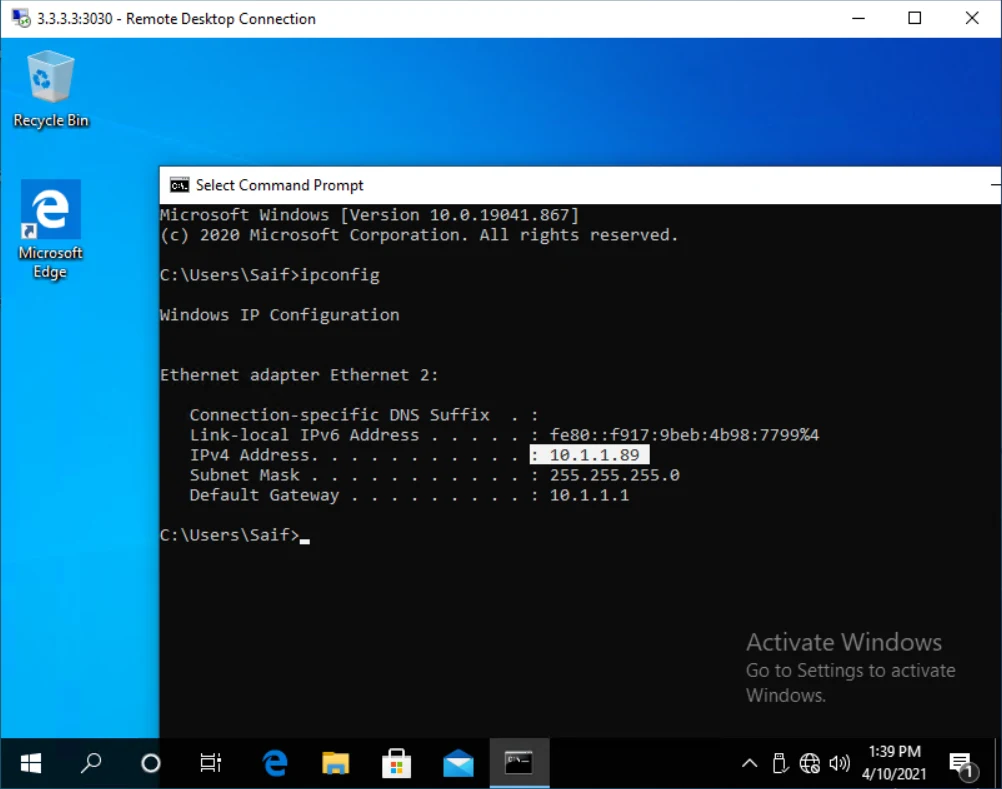
I have a network as shown below, where an RDP server is connected behind a pfSense firewall. I am going to allow an internet user with a public IP address of 1.1.1.1 to access the RDP server, which has a private IP address of 10.1.1.89.
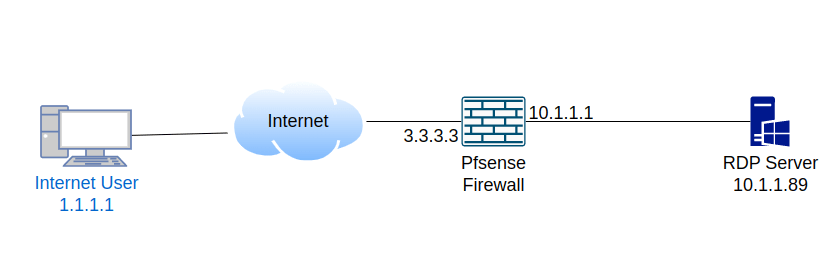
By default, you cannot initiate communication from the internet to a private LAN segment as it will be blocked by the firewall. To enable access, you need to create a hole in the firewall that will allow only the specific traffic to get into the private RDP server. This mechanism is called port forwarding, and it basically does destination NATting.
Test the RDP service lcoally.
before you allow any service on the firewall, it is important that you verify, is it allowed on the machine itself and am I allowed to RDP into the server locally. If the RDP service is not enabled locally you must set it up first and then proceed with the port forwarding configuration.
The common way to test the RDP from your local network is by using the telnet command as below.
telnet <IP address> <port number>If you are using windows and do not have telnet enabled, you must first enable the telnet on your windows host before testing with telnet command.
As you can see, I tried to telnet into the host in my LAN and it is working fine.
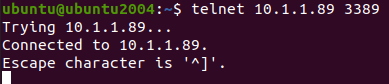
From my Ubuntu host, I also tried to RDP using remmina software and that worked perfectly fine as well.
Initiate RDP traffic from outside.
Even though I have RDP server with the private IP 10.1.1.89, when you tried to initiate the communication from outside/internet you should use the public IP address of your firewall. As the private IP’s are not routed to the internet.
From the host machine behind the public IP 1.1.1.1, I just initiated the RDP communication to the server which is in 3.3.3.3, as you can see it was kept trying unitl I stopped.
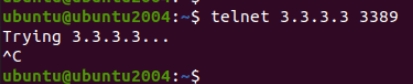
If you try to RDP into the pfsense outside public IP, you must get some logs on the firewall.
Check the Pfsense logs.
You can check the firewall logs by going into Status-> System-> Firewall.
Mostly in live network you will get a lot of denied traffics, so in order to see the specific traffic use the filter option and filter for any traffic that are coming from the source IP 1.1.1.1 (In your case, the IP that you are trying from)
As you can see I am getting some RDP traffic which are denied by the pfsense firewall by default.
We need to create some policies to allow this traffic to our RDP server inside.
Configure the RDP forwarding on Pfsense firewall.
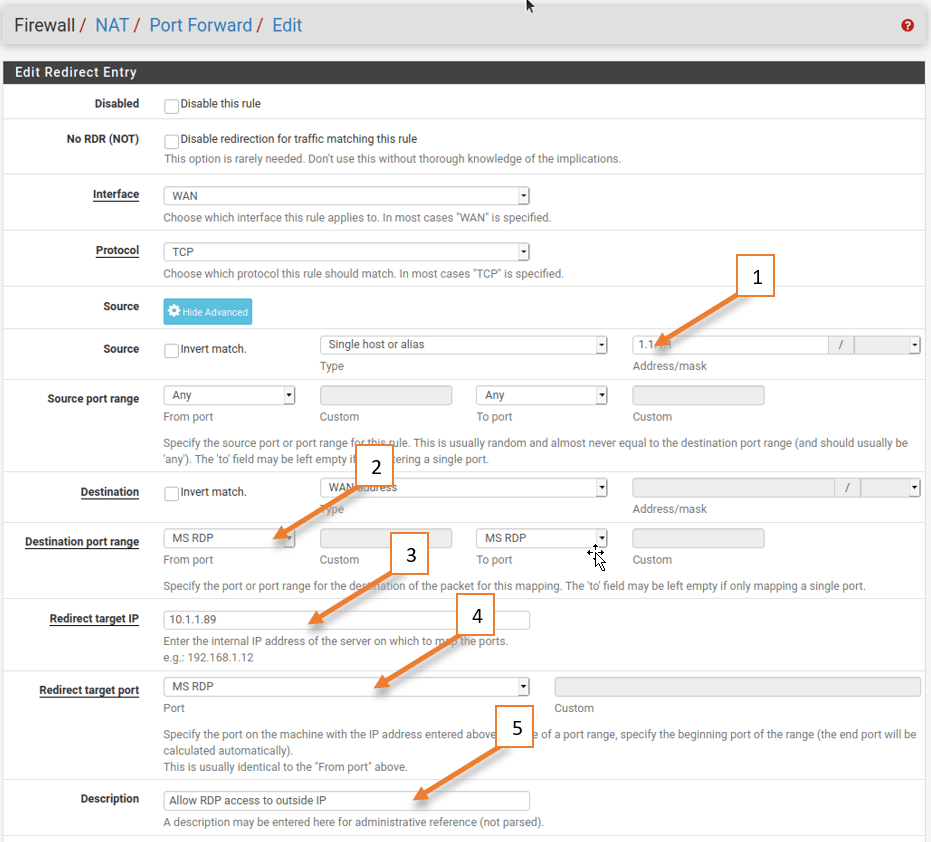
Before you proceed with the portforwarding, it is important for you to identify the source IP address, Destination IP address, and Destination port.
By following the steps above, we now got a below information.
Source IP : 1.1.1.1, which evident from the pfsense logs.
Destination IP: 3.3.3.3, of course, we already know this because this is our IP, and even the logs confirm the same.
Destination port : 3389 – which of course we know the standard RDP port number.
Note: You should never put any as source IP, which will put your entire network at risk.
As you may know we dont require the source port, which always be random.
lets now go ahead and add the portforwarding rule.
In the pfsense firewall, Click on firewall -> NAT -> Port forwarding.
Click on the Add rule at the bottom of any other rules.
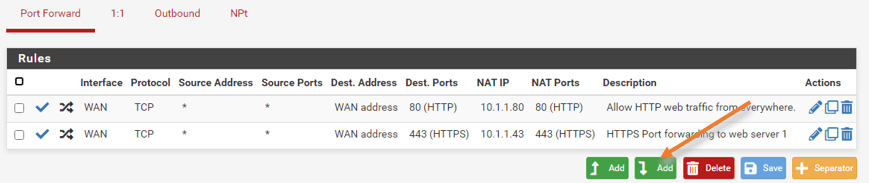
- Choose the source IP as 1.1.1.1
- Destination port range to MS RDP.
- Redirect Target IP to 10.1.1.89
- Redirect Target port to MS RDP.
- Give a description and save the configuration and apply the change.
Validate the RDP traffic on the firewall.
When you created the port forwarding rule, the pfSense firewall automatically created another security policy to allow the traffic. By default, this rule is not logged by default.
To see the traffic loggs on the newly created logs, we need to enable logging.
Allow rules logging.
Goto firewall>rules. Edit the RDP rule to log the session and apply the configuration.
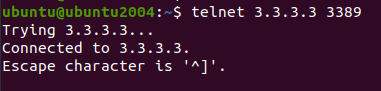
Test the RDP connectivity from outside.
I logged into the outside host which is 1.1.1.1, and using the telnet utility I can now verify the RDP port status and I can see it is open and connected. Which was failed before our change.
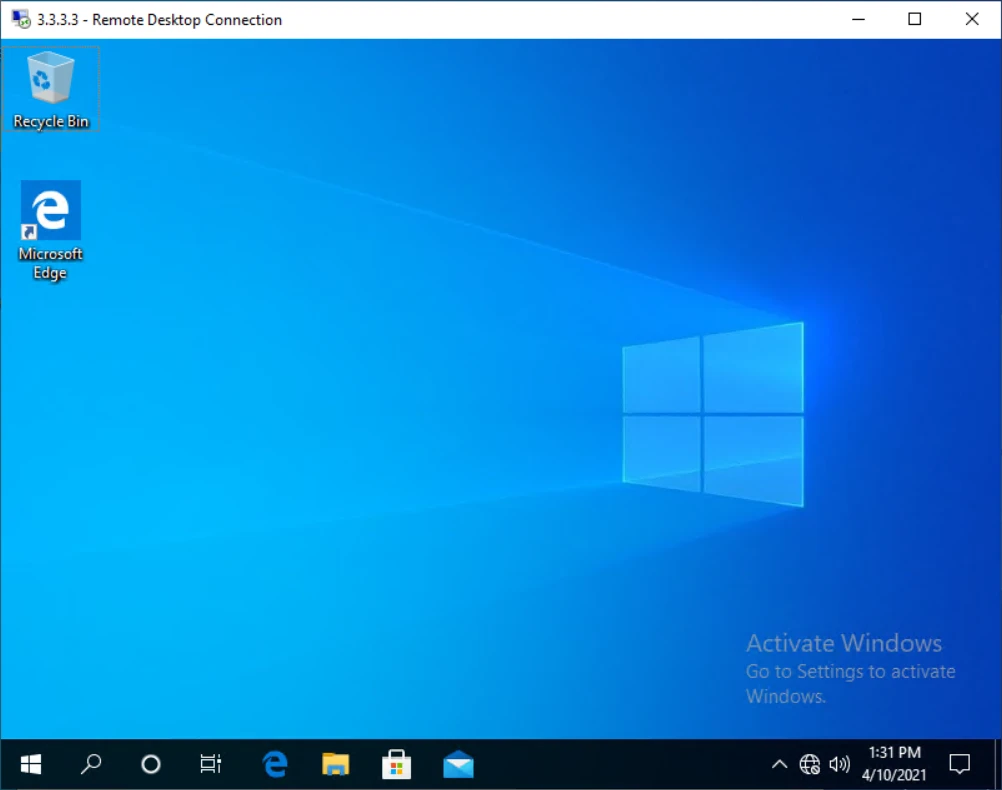
I also tried accessing the RDP access from the Windows machine using RDP client and that also worked just fine, and you can see the RDP IP is 3.3.3.3.
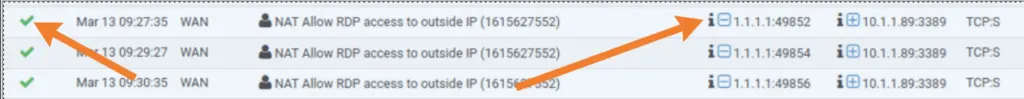
Since you allowed the logs, you can see the logs under status>system logs>firewall.
You can now see the logs for RDP access, and it is allowed to go inside.
Pfsense RDP port forward with a different destination port (port redirect).
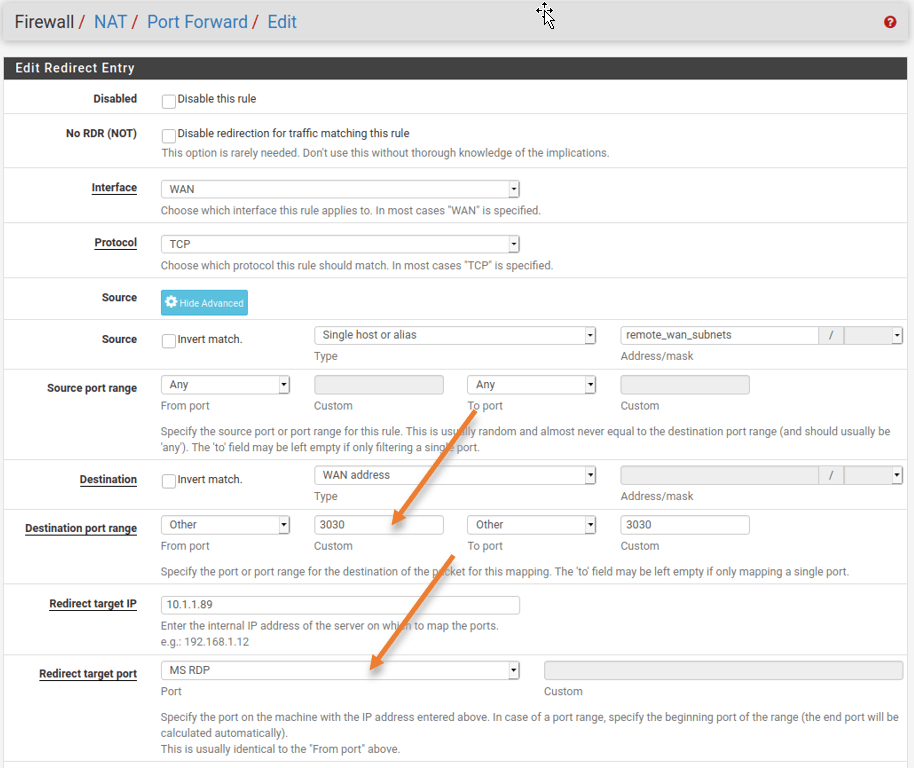
The port forwarding is working good and everyone is happy, but to tighten the security you decided to change the RDP machine port number from default port 3389 to 3030 and that would redirect to the destination port number to 3389 on the internal side.
For eg: The internet user is starting the session towards the WAN side 3.3.3.3 with the port number 3030 and the firewall should redirect the request to the internal RDP server with default port number 3389.
Internet user 1.1.1.1–> 3.3.3.3:3030 –>10.1.1.89:3389.
Let’s see how we can do that, go ahead and edit the RDP port forwarding policy.
- On the Destination port choose 3030.
- And Redirect target port choose the default RDP port which MS RDP.
Test the RDP redirect port connectivity.
Lets go ahead and test the connectivity now.
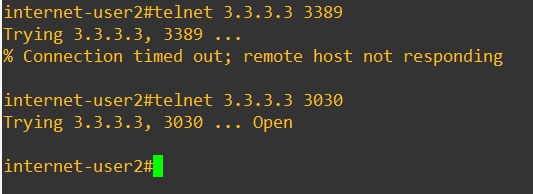
When I try to test the connectivity from the internet user the default RDP port is denied, however when I tried with the port number 3030 it is working fine. Let’s also check the RDP application.
How about from the RDP client?
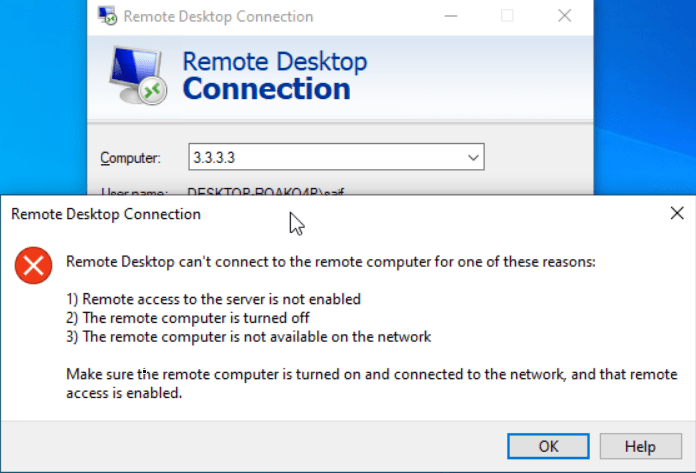
When I tried accessing the previous RDP configuration, I can no longer access the RDP machine and it says can’t connect.
So to connect with a different port number, while connecting instead of giving the just IP address, you can give the port number as well at the end of the IP address (3.3.3.3:3030)
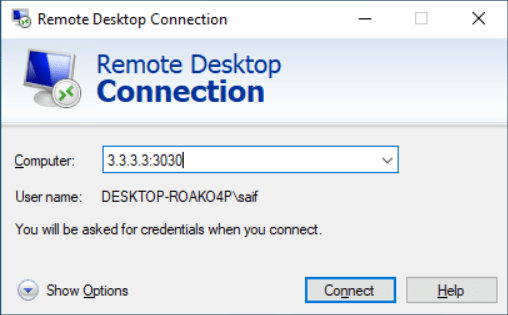
And the RDP access worked successfully after changing the port.