In the last blog post, we have looked at how you can configure Fortigate port forwarding for HTTPS, SSH, and RDP traffic. But that’s not the secure way to access the resources in the corporate network. If you want to have highly secure connectivity between two sides over the Internet, you either need to use a remote VPN or an IPSec site to site a VPN tunnel in a corporate environment.
Is it difficult to create an IPsec tunnel in FortiGate?
Unlike any other vendors, creating an IPSec site-to-site VPN tunnel between the Fortigate firewall is way too easy, even for a beginner who never created an IPsec tunnel. You don’t have to worry about the IPsec encryption and authentication algorithm that you need to use. Just open up the IPsec wizard and it is just a few simple clicks your IPsec tunnel is ready.
You can create multiple IPSec VPN tunnels between the sites. The traffic that is sent through the tunnel will be encrypted. If someone were to sniff the packet, they would see the public source and destination IP address, and they don’t see the inside packet. Instead, it will show you as an ESP payload. We have created multiple IPSec tunnels between the sites using different vendors. Such as Palo Alto Firewall, PFSense Firewall, Cisco routers, and so on. And in this blog, we will create an IPsec tunnel between two Fortigate firewalls.
Read also,
How to Setup IPsec Tunnel between Paloalto and PFsense?
How To Configure Palo Alto Site To Site VPN Using IPsec?
How To Configure IPsec VPN Between pfSense And Cisco Router?
How To Configure IPsec Site-to-Site VPN On Cisco Router?
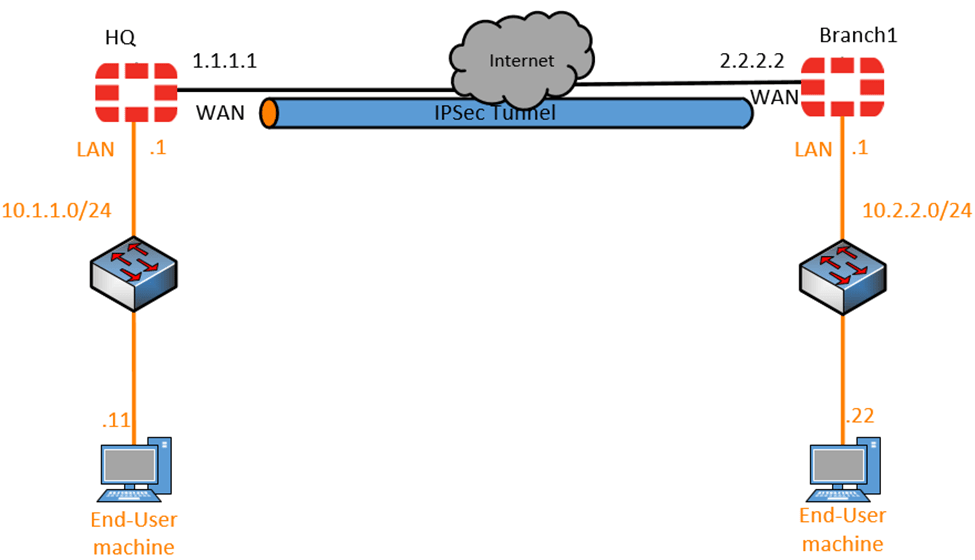
Below is the topology that we are going to use. We have a headquarter with a network of 10.1.1.0/24, and the branch has 10.2.2.0/24. Both the network can go out to the Internet. We can assume the WAN site IP address is 1.1.1.1 and 2.2.2.2, for HQ and Branch1 respectively. However, the HQ network cannot talk to the branch network at this moment. We will create an IPSec tunnel, after the tunnel is built. Both the HQ and branch LAN sides will be able to talk to each other. We will test the connection from both the end-user machines. On branch1 we have a windows machine and branch2 we have a Linux user using an Ubuntu machine.
Steps to configure Site to Site IPsec VPN on Fortigate.
- Configure the HQ IPsec tunnel.
- Configure the VPN setup.
- Configure the authentication.
- Configure the policy and Routing.
- Review the configuration.
- Branch1 IPsec tunnel configuration.
- VPN setup configuration.
- Athentication parameters.
- Configure the branch1 policy and routing.
- How to check ipsec tunnel status in fortigate?
- Enable logging for the IPsec policy.
- Test the traffic.
- How to delete Ipsec tunnel in fortigate?
Configure the HQ IPsec tunnel.
We will create the HQ IPSec tunnel first, then we’ll proceed with the branch1 IPSec tunnel.
Configure the VPN setup.
Log into the Fortigate firewall and go to VPN-> IPSec Wizard.
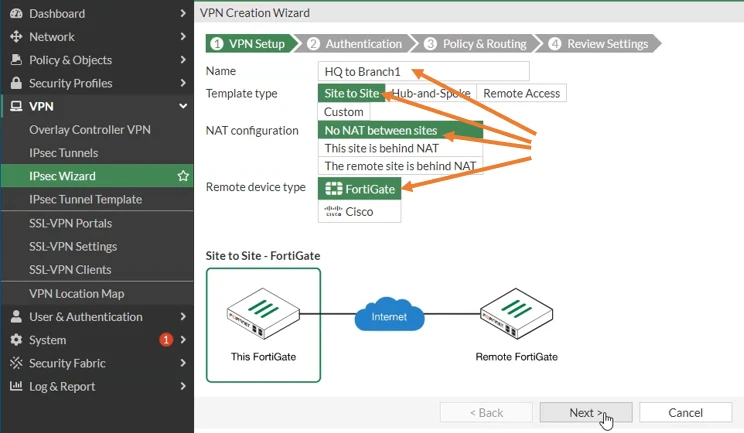
Name: HQ to Branch1
Template Type: Site to Site.
Nat configuration: No NAT between sites.
In our setup, both the Branch1 and the headquarters are directly connected to the internet with public IP and no NAT device in front. So you may choose No NAT between sites. In case your firewall is behind a NAT device, then you need to choose the appropriate settings.
Remote device type: Fortigate.
And you may click on next.
Configure the authentication.
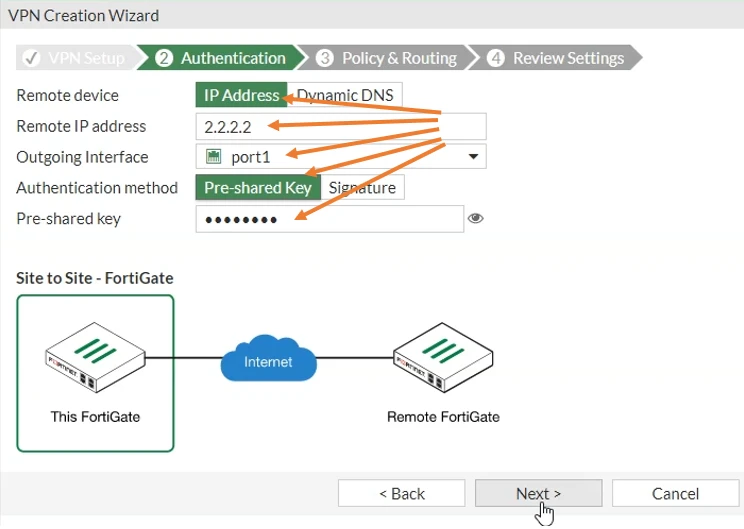
Remote Device: IP address – You have to choose the remote device as IP address
Remote IP address: 2.2.2.2 – In the remote IP address field you have to put the IP address of the remote location. This is a public IP, not a private IP.
Outgoing interface: port1 – Which is the WAN interface of our local firewall.
Authentication method: Pre-shared key.
Pre-shared key: You can create an IPSEC tunnel using the Preshared key or with a certificate. The pre-shared key is a very common one and hence we are going to choose the same. So choose a pre-shared key and enter the key here. You need to ensure both sides should match.
So after you did that, you may click on next.
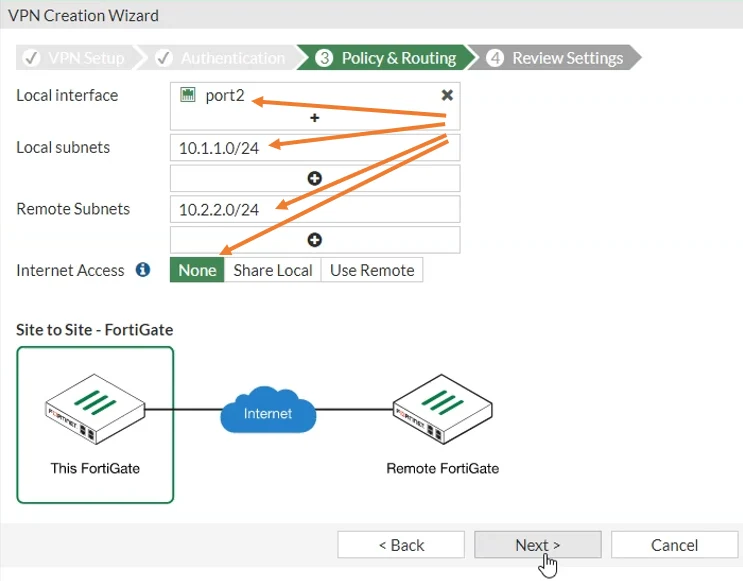
Configure the policy and Routing.
We are now going to create a policy and routing for the firewall, this is how the routing happens on the IP sec tunnel.
Local Interface -> Port2- you need to specify the local interface so the LAN side of the firewall which is port two.
Local Subnets -> 10.1.1.0/24 – and your local subnet will be automatically populated upon chooseing the local interface.
Remote Subnets -> 10.2.2.0/24 – For the remote subnet you have to manually type that in the IP address, which is 10.2.2.0/24
Internet Access -> None
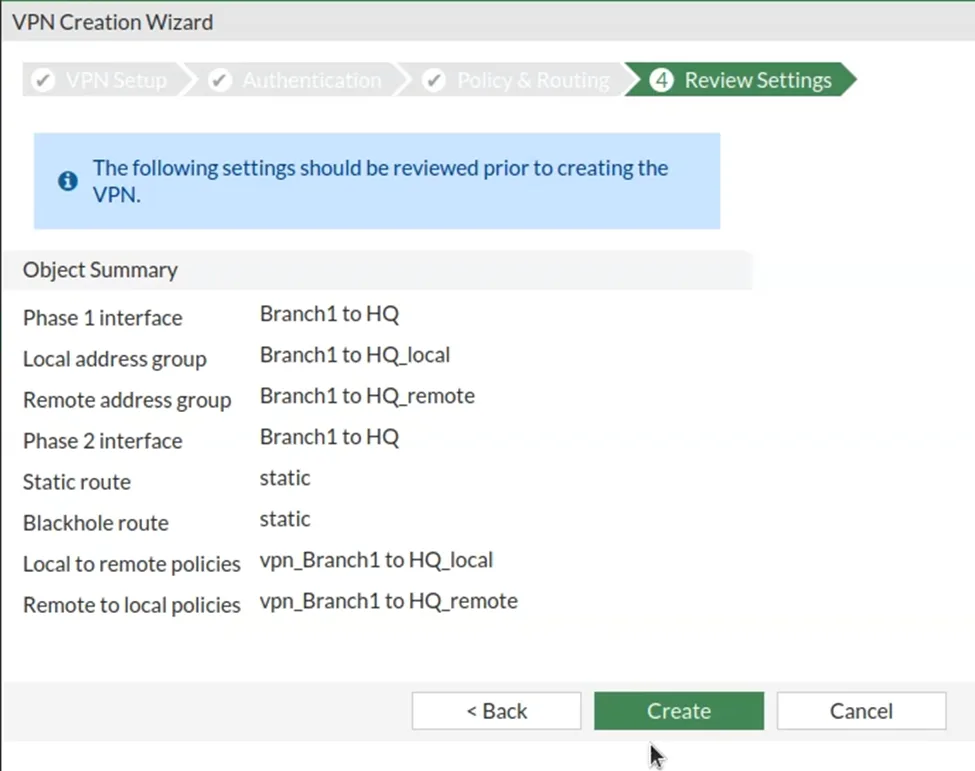
Review the configuration.
So finally you will get the phase one and phase two parameters summary of the configuration. Just make sure everything looks good and after you verify the configuration, you may click on create. Any modification is required, you may click on the back button.
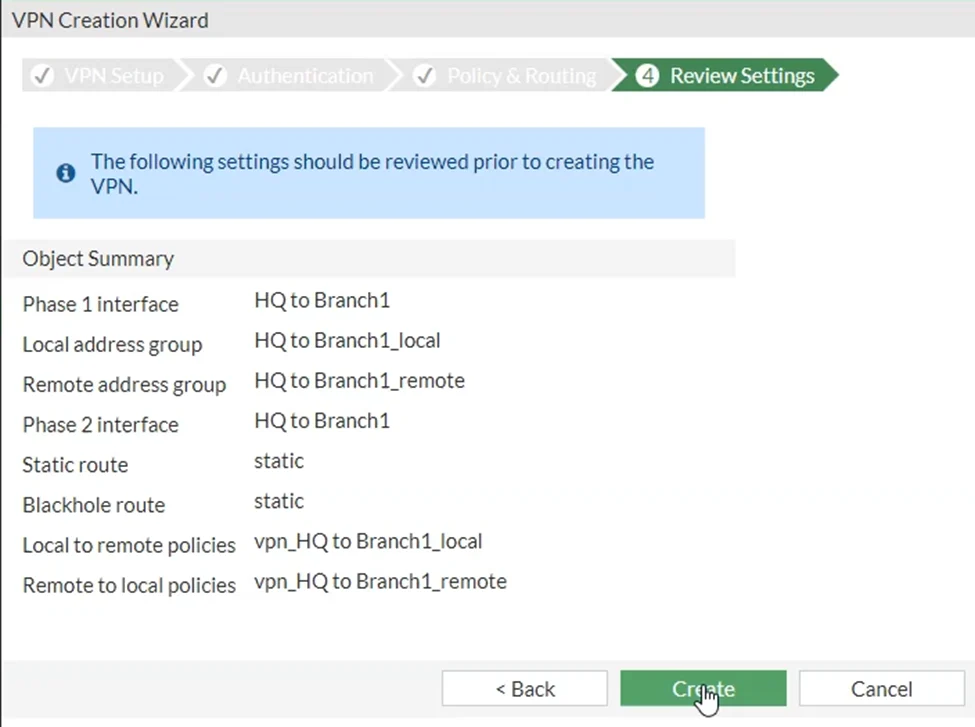
After a few seconds, you’ll get a message that says the VPN has been set up and that’s it. You just completed the HQ configuration of the VPN.
You can click on show tunnel status to see whether the tunnel is up or down.
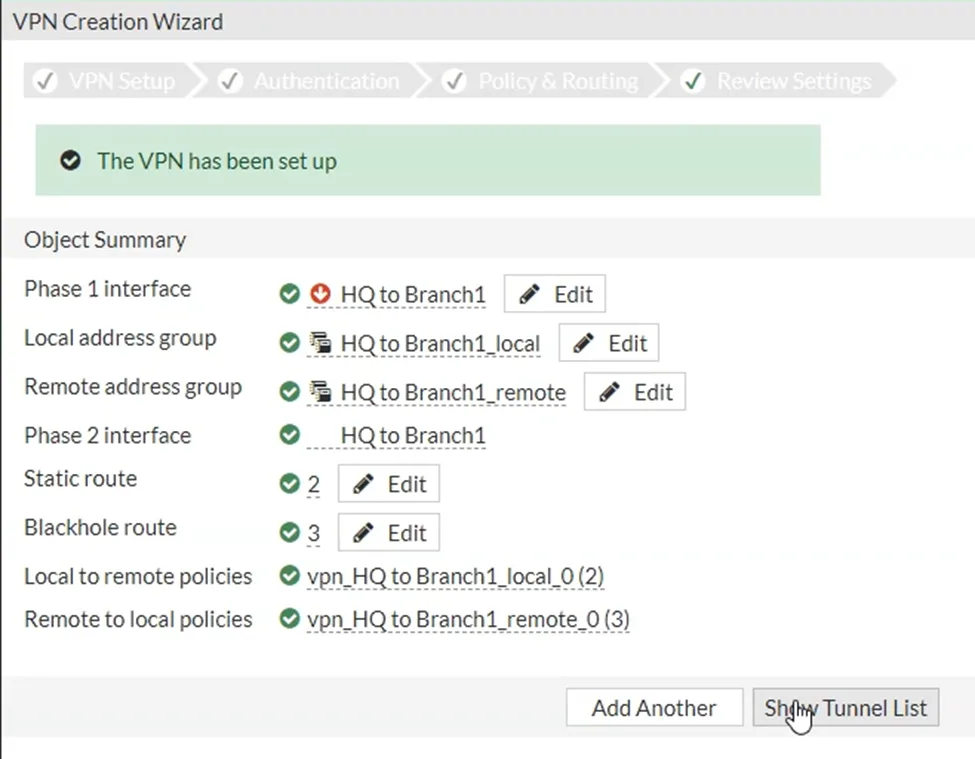
Of course, it will be down at this moment because you haven’t configured really anything on the remote side.
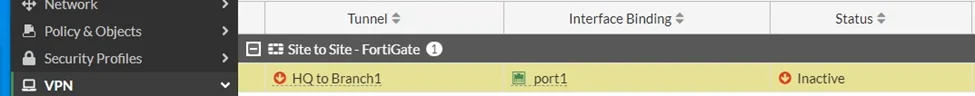
Alternatively, you can go to the dashboard and network where you can choose your IPsec tunnel from there.
If you have configured both sides, you can select the IPSEC tunnel and click on bring up to bring up the tunnel which we will do it later, once you have the branch side of the configuration is completed.
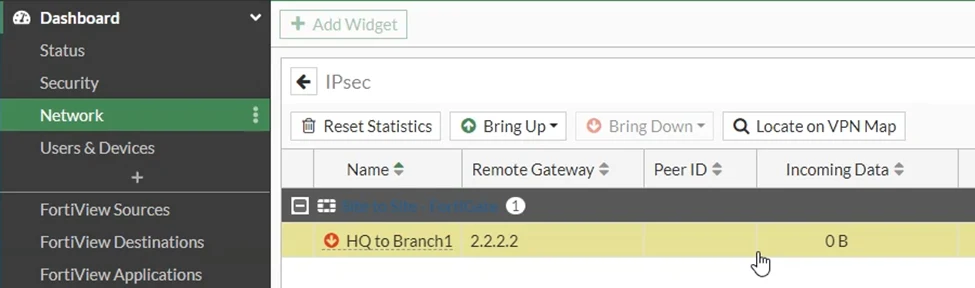
Branch1 IPsec tunnel configuration.
Just like we did the HQ configuration, we’ll have to do the same thing for the branch side as well.
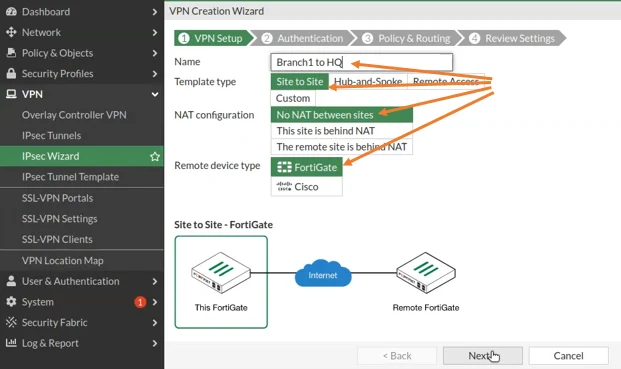
VPN setup configuration.
Log into the Fortigate firewall and in that under VPN -> Ipsec Wizard.
Name: Branch1 to HQ
Nat Configuration – No Nat between sites.
Remote device type – Fortigate
And click on next.
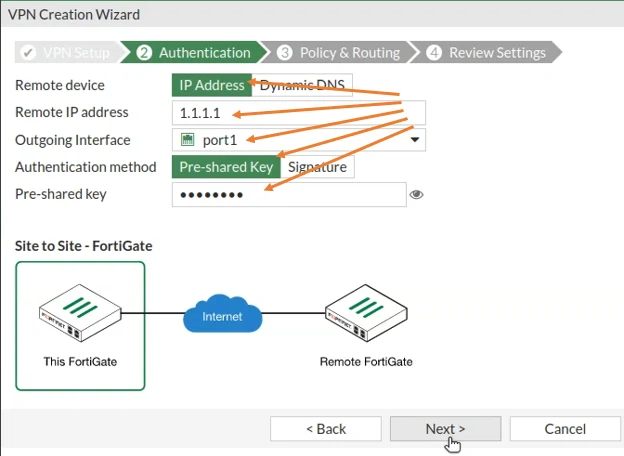
Authentication parameters.
In the authentication parameters, you have to choose the following.
Remote device as IP address
Remote IP address -> 1.1.1.1- which is a headquarters WAN side IP address, so it should be always a public IP that you have to type. So again, if you have a another Nat device or a router infornt of the firewall. You’ll have to enter the public IP of the remote device because only through public IP you can communicate from one side to another over internet.
Outgoing interface-> Port1 -> the Wan interface of the firewall.
Authentication method-> Pre-shared key.
Pre-Shared key -> Enter the pre-shared key here which is the same as the HQ one.
click on next.
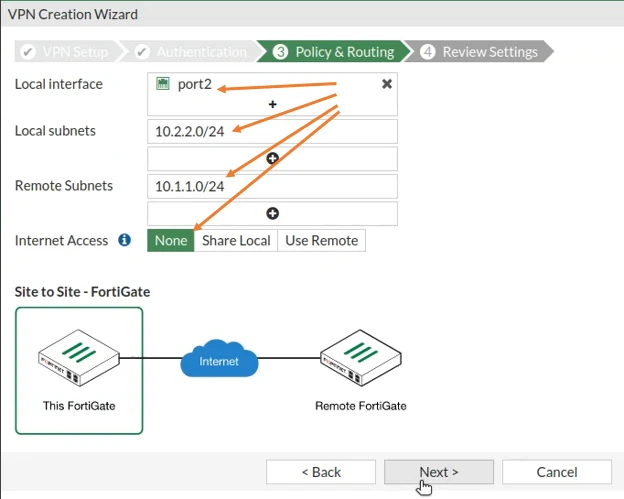
Configure the branch1 policy and routing.
Local interface -> Port2 – similar to the headquarters policy routing. You’ll have to choose the local interface as the LAN side, which is a Port 2.
Local subnet -> 10.2.2.0/24 – This has already picked up when you chose the local interface.
Remote subnets -> 10.1.1.0/24 – You need to manually define the remote subnet switches 10.1.1.0/24.
And the Internet access should be none. And after that you may click on next.
You’ll get the summary of the configuration if you want to make any modification, you may click on the back button. So if you’re fine you may click on create to create the IPSEC tunnel and after a few seconds the tunnel will be created and you will get a message that says the VPN has been set up.
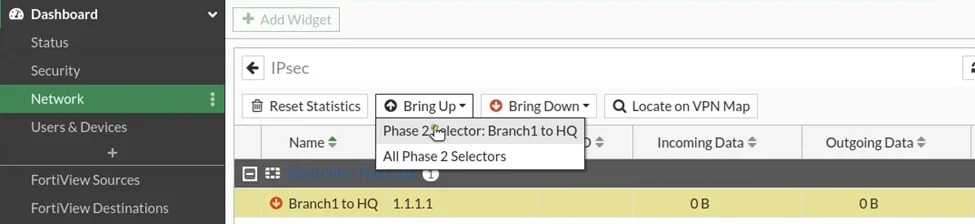
How to check ipsec tunnel status in fortigate?
To check the IPsec tunnel status and bring up the tunnel, You can initiate the traffic from either the branch or HQ LAN side. Alternatively, you could go to dashboard -> Network -> Scroll down, you will see IPSEC tunnel on the list. once you select the IPSEC tunnel you may choose to bring Up -> phase two selector Branch1 to HQ.
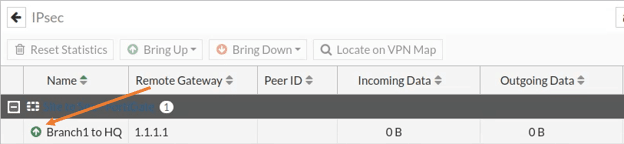
As you can see the tunnel just came up and there are no traffic yet on the IP sece tunnel, as you can infer from the incoming and outgoing data which is shows 0bits.
Enable logging for the IPsec policy.
Right after you build the IPsec tunnel there will be rules created for the traffic that is going in and out of the IPsec tunnel. But you can only see those traffic in the fortigate logs, after enabling the all session loggins.
On the HQ firewall ->Goto Policy& Objects -> Firewall Policy.
You will see two rules, the one that is allowing the traffic coming from the branch1 to the LAN side of the HQ, and the second one is allowing the traffic from HQ LAN to the Branch1 remote.
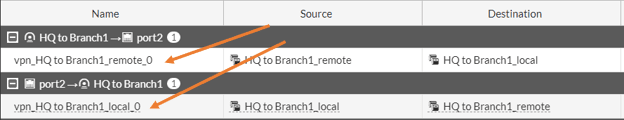
- Double click on the first rule.
- Scroll all the way down, and check Log allowed traffic option is checked, and the All sessions are selected.
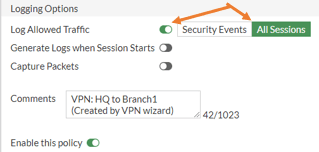
- Do the same thing for the second rule, as well as on the branch1 firewall.
Test the traffic.
Let’s initiate some traffic from the headquarters to the branch.
From the HQ, let’s ping branch one and host IP address which 10.2.2.22. And as you can see how we are able to reach the IP just fine.
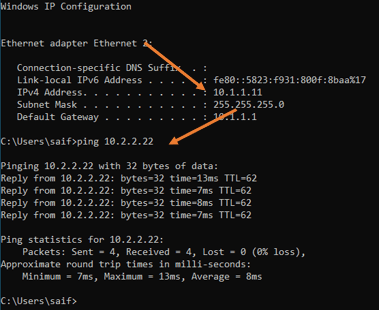
And the traceroute shows the packet is taking the ipsec path.
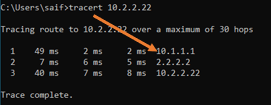
That is from branch1 to branch2 communication, how about other way around?
From Ubuntu let’s try to ping the windows machine
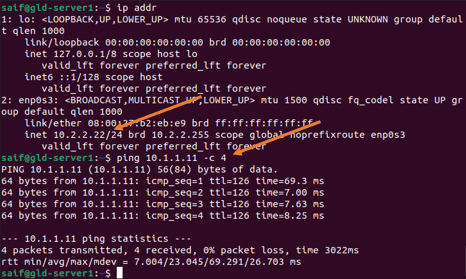
How to delete Ipsec tunnel in fortigate?
When you try to delete the IPsec tunnel in fortigate, you will see that the delete option is grayed out. Actulaly deleting option grayed out is a good thing, because no one will be able to delete the tunnel by mistake. And the reason you see the delete option is grayed out, cos you need to remove the associated configuration in order to delete the IPsec tunnel.
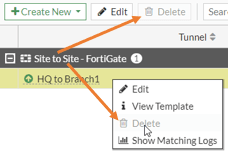
1. First Delete the static route.
Goto Network-> Static route.
Select the two associated static routes from the list.
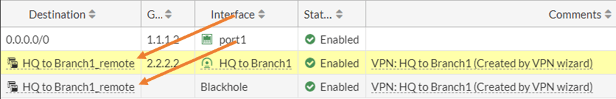
2. Delete the policy.
Similarly, remove the policy associated with the tunnel.
After both are removed, you can come back to the IPSec tunnel screen in VPN->IPsec Tunnels
You will now see the delete option is available for you to remove the IPsec tunnel.