In my previous blog, we have covered plenty of articles related to the pfsense firewall, which is a great firewall if you want to use it for your home purpose. However, suppose you’re going to use it for commercial use. In that case, you cannot use custom hardware with pfsense in it. As per the netgate terms of service, the company that develops and manages the pfsense firewall says you should not use the community editions of the pfsense firewall for commercial use. You should use pfsense plus instead, which is only available on netgate hardwares and on the cloud.
When it comes to fortigate Firewalls, it is not open-source. It is a commercial firewall that is only available for purchase. Though they have a free trial of 16 days, you cannot do anything much on that. For example, in the case of IPsec, it doesn’t support all the IPSec parameters on the fortigate free trial.
I am running pfsense on my home network, and in this blog, I will build an IPsec tunnel from a fortigate firewall to a pfsense firewall.
Below is the topology that we are going to use.
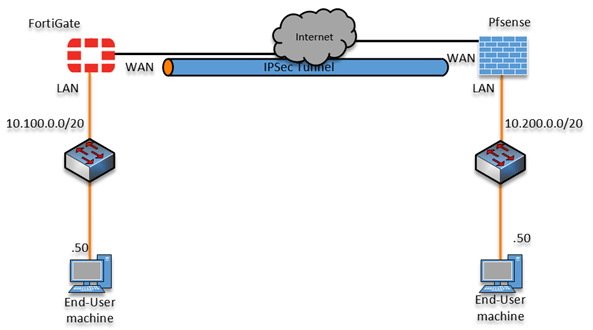
We have a fortigate firewall with a LAN network of 10.100.0.0/20, and pfsense got 10.200.0.0/20. Both networks can go out to the internet, but they cannot communicate with each other. To put it simply, you can think of a fortigate network as one company, and you acquired another company that uses a pfsense firewall. Fortunately, both are using different networks, and you don’t need to worry about subnet conflict.
With that, let’s go ahead and build an IPsec tunnel from a fortigate firewall to a pfsense firewall.
IPsec configuration on fortigate.
The IPsec Tunnel consists of two phases, phase one and phase two. Phase one is connectivity between the Internet side, and phase two takes care of the data traffic.
Fortigate Phase1 configuration.
Let’s go ahead and configure phase one of the IPsec.
Log into the Fortigate Firewall, under VPN->IPSec wizard.
You may name the tunnel name and choose the template type as custom. And click on next.
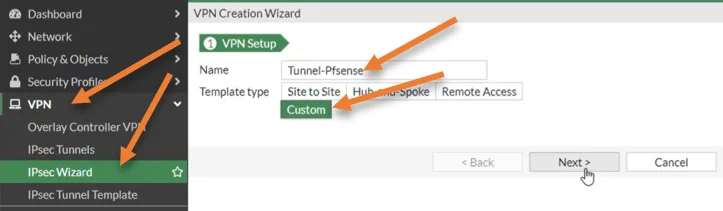
Name : Enter a name for the tunnel.
Comments : To identify the tunnel, will be useful if you have multiple IPsec tunnels.
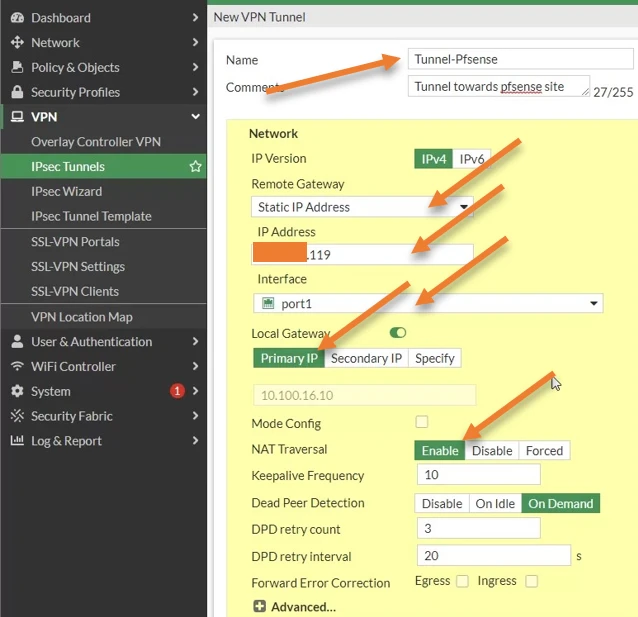
Network
IP version: IPv4>
Remote Gateway: Static IP address.
IP address: Enter the Public IP address of the Pfsense firewall.
Interface: Choose the WAN interface connected to the internet side of the fortigate Firewall, in my case it is port1.
Local gateway: Choose Primary IP. It would automatically pick up the public IP address configured on port1. In my case, the Firewall is behind the NAT gateway. Hence I have a private IP address instead. I also allowed port 4500 to reach the fortigate WAN interface on my NAT device.
NAT Traversal : I choose Nat Traversal enabled since the fortigate is behind the NAT.
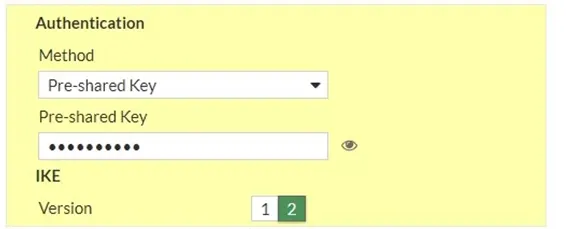
Configure the Authentication.
You can create an IPsec tunnel with a preshared key or a certificate. The very common method is to use the preshared key; hence choose a preshared key and enter the pre-shared key.
You need to ensure the pre-shared key matches on the Fortigate and pfsense sides.
Configure the Phase1 proposal.
You will see multiple phase 1 proposal are selected. However, you don’t need to choose all of them.
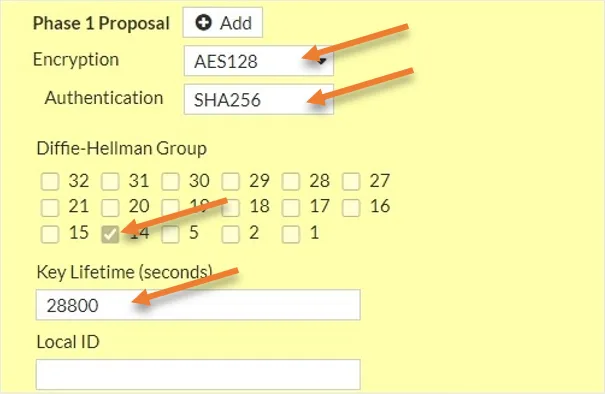
We will specify the phase one proposal in the encryption and authentication and the Diffie Hellman group. The same will be configured on the other side. I’ve seen many people use sha1 as the authentication, but that’s not recommended. So instead, we choose SHA256.
Encryption : AES128
Authentication: SHA256
Diffie-Hellman Group: 14.
That’s a secure Phase1 configuration.
Fortigate phase2 configuration.
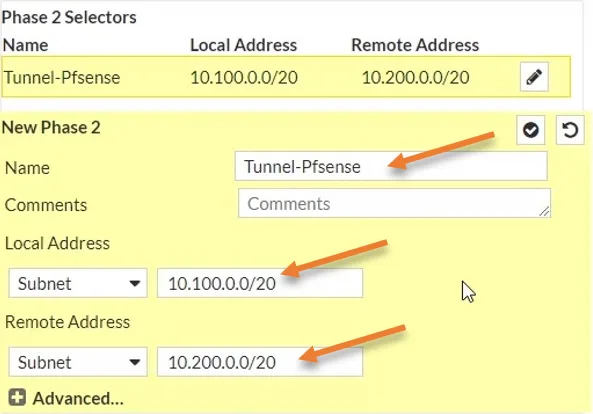
You need to configure the interesting traffic here, so you need to choose your Local network subnet and you also need to choose the remote LAN as well. It will ensure that only traffic matches these subnets will be allowed through the IPsec tunnel.
New Phase2.
Name: Enter a name for the phase2.
Choose the Local subnet and remote subnet.
Click on Advanced.
Configure the phase2 proposal.
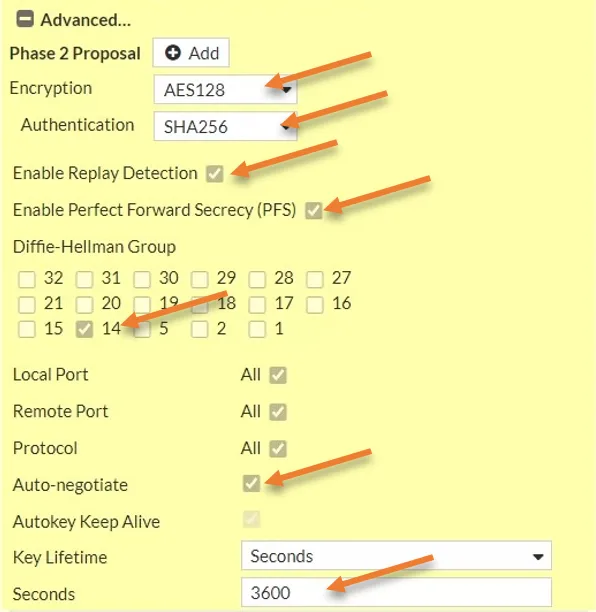
Like we made the phase one proposal, you also have to configure the phase 2 proposal.
Encryption : AES128
Authentication: Sha256.
Check the following options.
Enable replay detection.
Enable perfect forward secrecy.
Diffie Hellman Group: 14.
Key lifetime: 3600 seconds.
We just completed the Fortigate side of the IPsec tunnel. Let’s move on to the PFsense side of the configuration. And like before, we will start with phase one of the IPsec configuration.
Login to the Pfsense->VPN->IPsec-> Click on Add phase1.
Pfsense Phase 1 configuration.
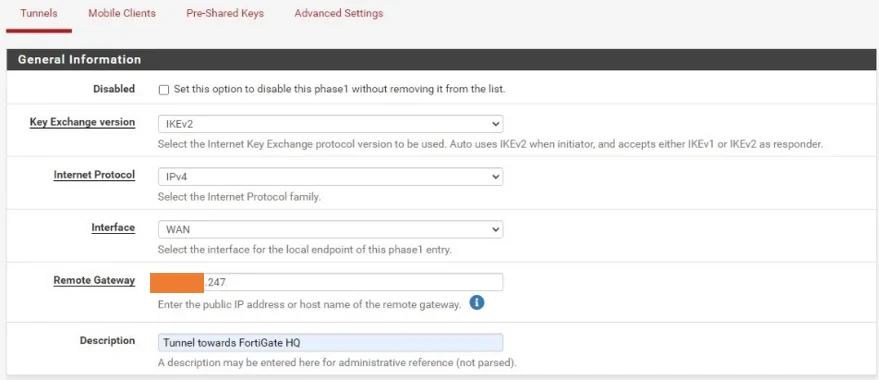
Choose the Key Exchange version as IKEv2.
Interface : WAN.
Remote Gateway : Enter the public IP address of the fortigate Firewall.
Description : Add a user friendly description.
Phase1 proposal – Authentication.
Authentication Method : Mutual PSK.
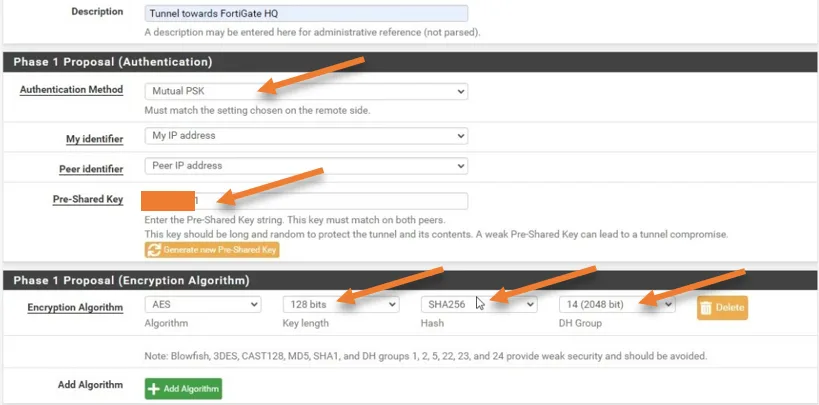
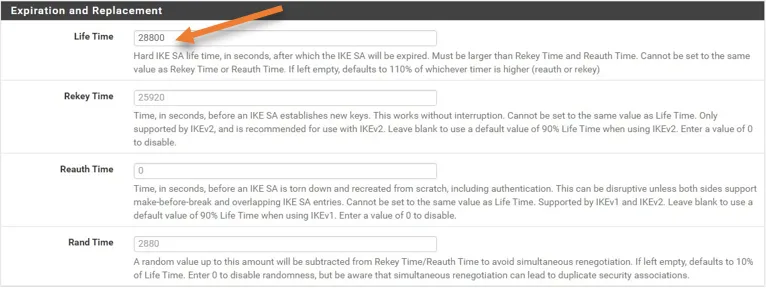
Under Expiration and replacement, add the lifetime as 28800 seconds.
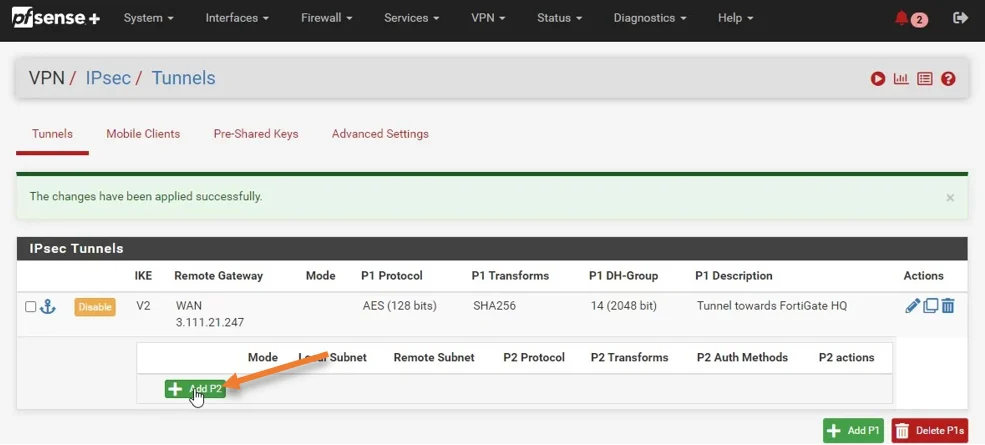
Pfsense Phase2 configuration.
We just completed phase 1 of the IPsec configurations. Let’s go ahead and do phase 2 of the configuration.
To add phase two, click on add P2.
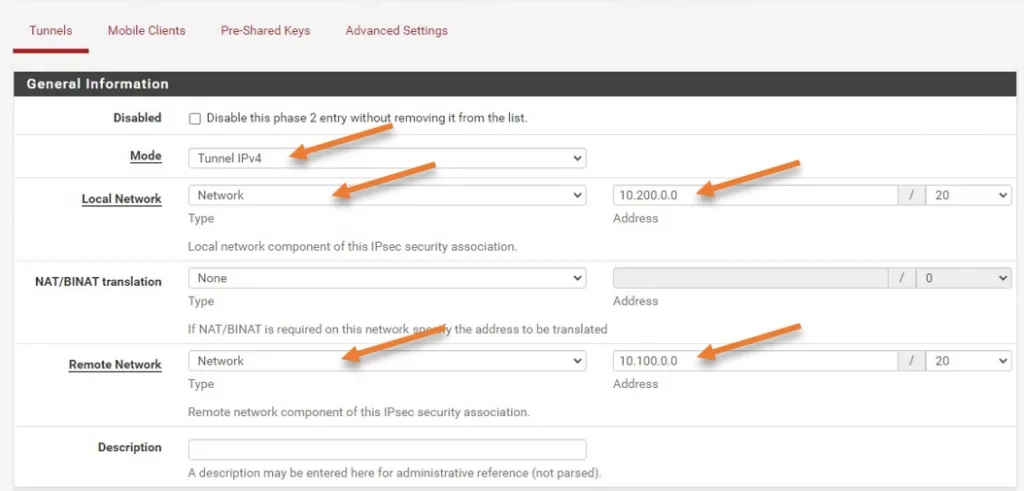
Like we configured the interesting traffic on the Fortigate, you’ll have to do the same thing on the PFsense side.
Local Network: you can choose a LAN Address as the local Network or choose Network and specify the subnet.
I have chosen Network and typed the subnet as 10.200.0.0/16
Remote Network: you need to specify the remote Network here. In this case, it’s 10.100.0.0/16.
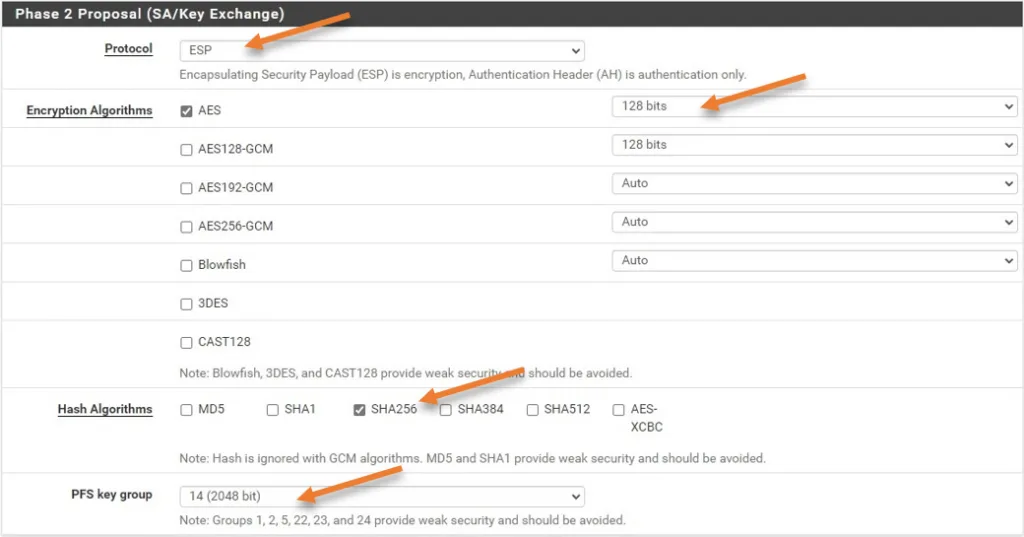
Phase 2 Proposal.
In the phase 2 proposal, choose the protocol as ESP.
Encryption Algorithms : AES 128bits.
Hash Algorithms : Sha256
PFS Key group : 14 (2048bit)
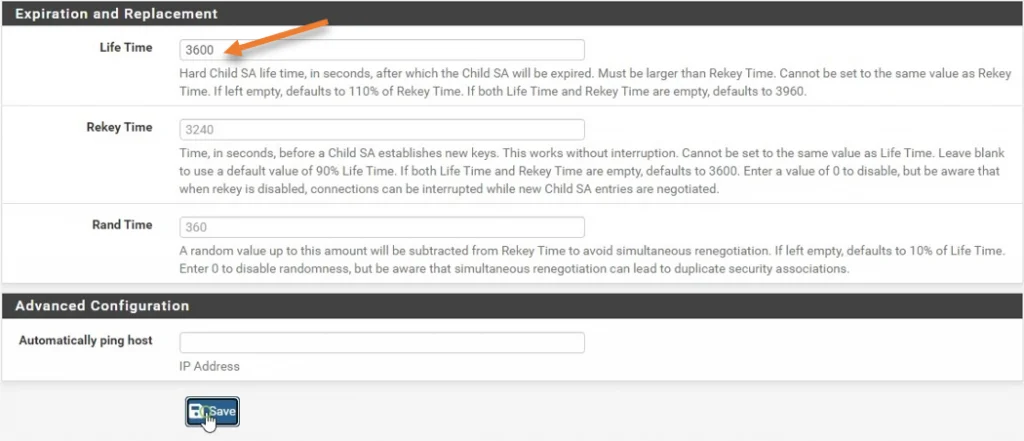
Expiration and replacement.
Enter the phase 2 life time as 3600 seconds, same duration we configured on the fortigate.
Click on Save.
Note : You can also mention the remote IP address so the Pfsense will send continuous ICMP traffic to the host.
Configure the Security Policy on fortigate.
We configured the IPSec tunnel on both sides. However, in Fortigate, you must configure the security policy to allow the traffic and the static route towards the tunnel.
The good thing about the PF Sense firewall is that it already has the policy pre-configured and the routing also done, so you don’t need to do anything much on the PFsense side.
Configure the policy to allow traffic from LAN to Ipsec.
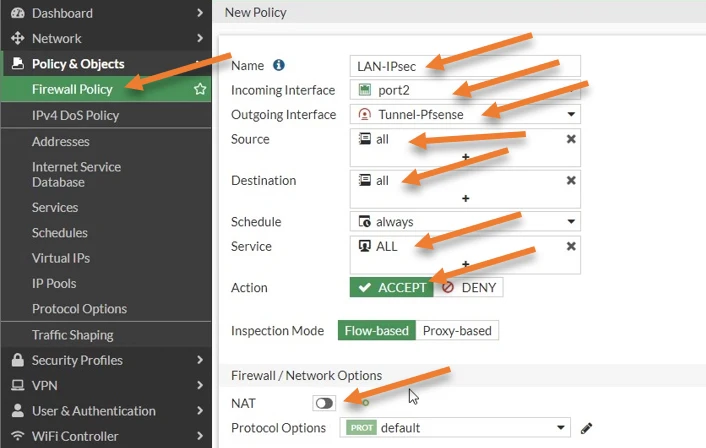
Goto Policy & Objects-> Firewall Policy -> Click Create new
Name : Enter the name for the policy>
Incomingn Interface : Choose the LAN side of the fortigate Firewall.
Outgoing Interface : Choose the ipsec tunnel interface that we just created.
Source : You can create a address object and choose that address object as the source, however I am choosing all the traffic.
Destination : choose All as the destination as well.
service: All.
Action : Accept.
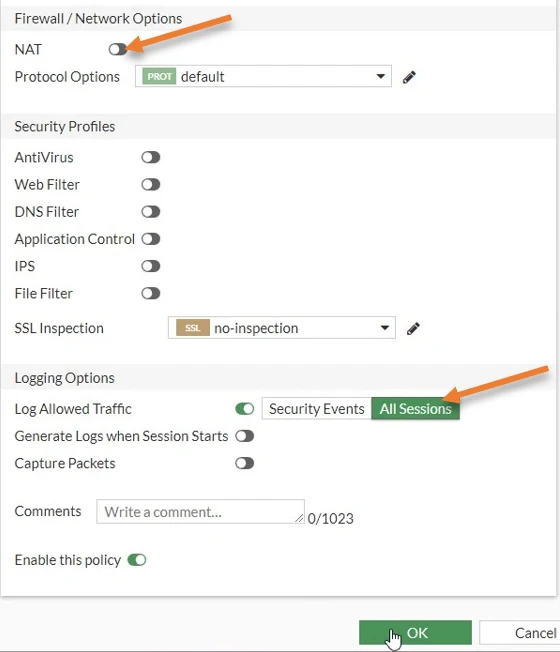
NAT : Uncheck.
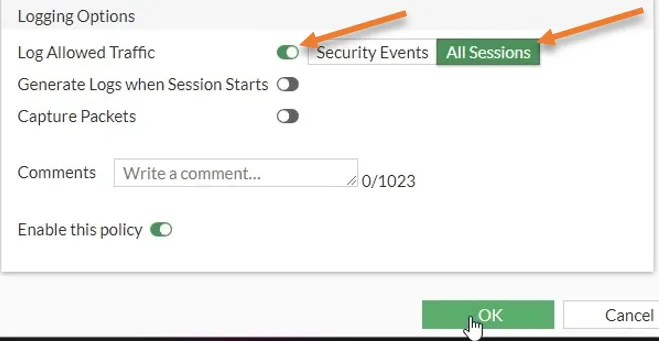
To see all the traffic traversing across the IPSec tunnel, you must log all the sessions. Check the option log allowed traffic and choose all sessions.
Click on Ok.
Configure policy for the traffic coming from the IPsec to the LAN.
We configured the policy from LAN traffic that is going across the IPSec tunnel. Now we need to do just the opposite: the traffic coming from the IPSec tunnel to the LAN side has to be allowed as well.
Click on create new on the firewall policy.
Name IPsec-LAN.
Incoming interface: Choose the IPsec tunnel interface.
Outgoing interface: Chose the LAN side of the Firewall.
Source: All.
Destiantion: All.
Service: All.
Action: Accept.
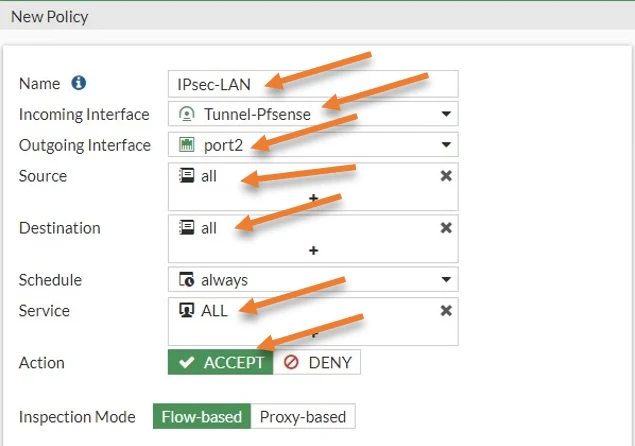
Uncheck the Nat option.
to see the traffic, Check the Log allowed traffic option, and choose All sessions and click on Ok.
Configure the static route.
We allowed the traffic through the IPSec tunnel. But we need to tell the Firewall if you want to send traffic to the 10.200.0.0/16 network, it has to go via the IPSec tunnel. The way we tell Firewall is by configuring a static route.
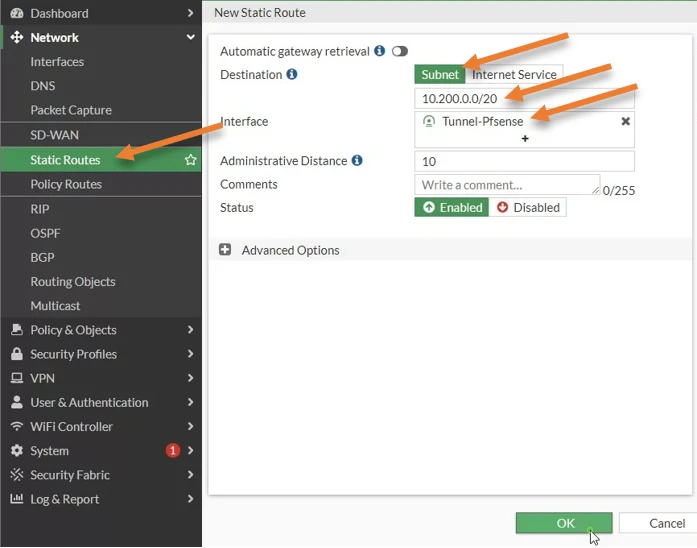
Goto Network-> Static route-> Create New.
Destination : Subnet.
Enter the 10.200.0.0/20 network.
Interface: Chose the tunnel interface, which is Tunnel-pfsense.
Status: Enabled.
Click on Ok.
The static route will be added to the Firewall.
Did you notice, when I chose the tunnel interface, it showed green color instead of red ?, that’s because, while we were making the changes, the tunnel already came up.
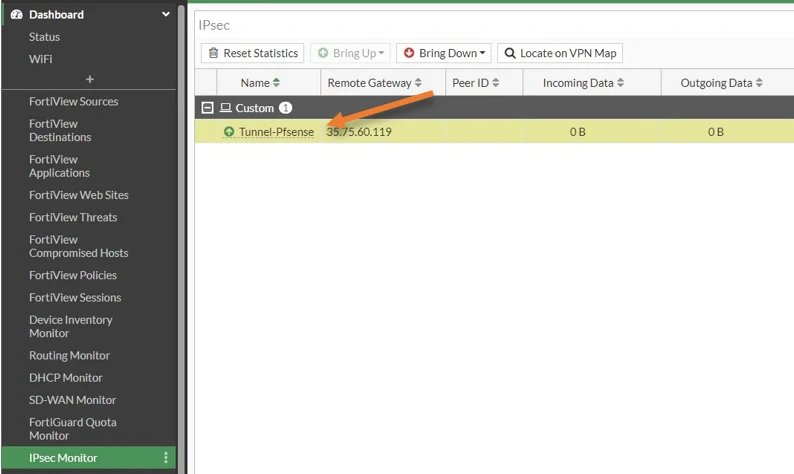
Check the tunnel status on both the pfsense and fortigate.
That’s it, you have configured IPSec tunnel on the Fortigate to Pfsense, to see the tunnel status, you could go to dashboard and Network. And you can choose the IPSec tunnel from there where you will be able to see the status of the IPSec tunnel status and if you are using a comprehensive dashboard, you can go to the dashboard and choose IPsec monitor, and you’ll be able to see the tunnel over there.
In case the tunnel hasn’t come up yet, you may choose a tunnel and click on Bring up options.
Similarly, to see the status on Pfsense, you can click on status-> IPSec, and you’ll be able to see the status of your IPsec tunnel. As you can see, it is an established state, on both phase one and phase two of the tunnel.
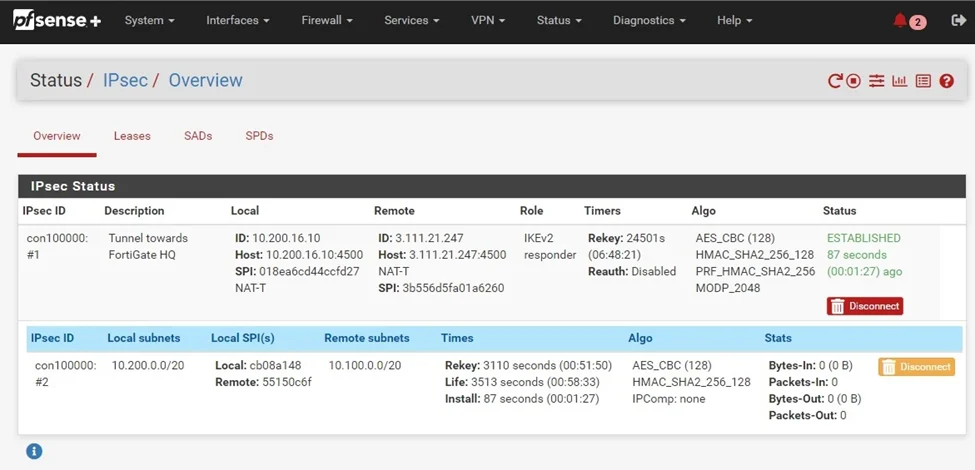
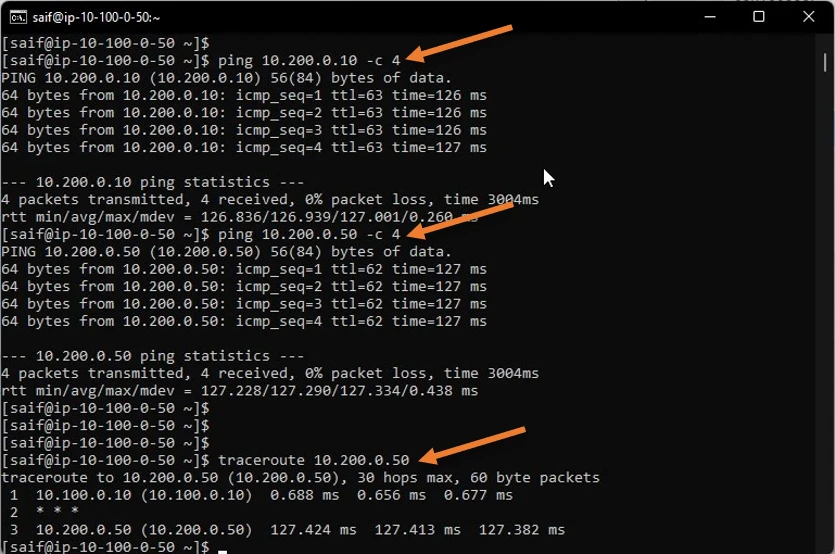
Test the IPsec communication.
To test traffic, you can initiate traffic from either side towards the remote, and if you have configured everything correctly, you will see the traffic is going across the tunnel.
The tunnel has been working fine. As you can see, I was able to ping from a Local client, 10.100.0.50 to the remote side IP address 10.200.0.10, which is the PFsense LAN side IP address and one of the other hosts on the LAN side 10.200.0.50, and it worked just fine.
I also did a traceroute that shows the traffic going through the tunnel.
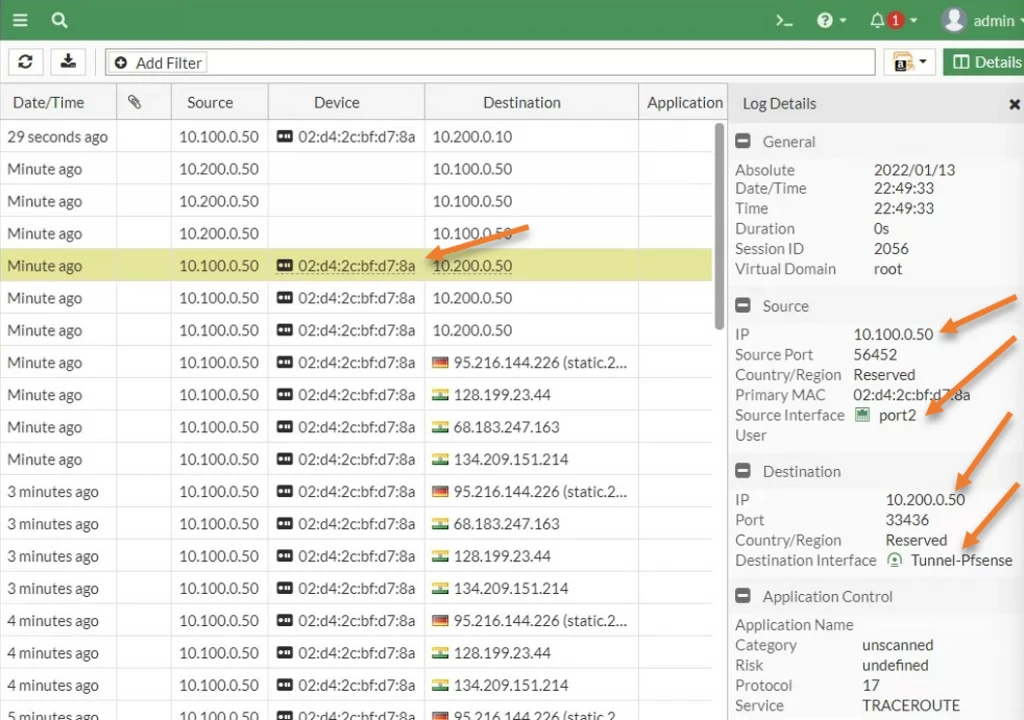
Check the logs on fortigate.
You can also observe the same traffic inside the Firewall. I have initiated some more traffic, and if I go to log and reports->Forward logs: We should be able to see all the logs going through the IPsec tunnel because we have the log forwarding enabled for all sessions.
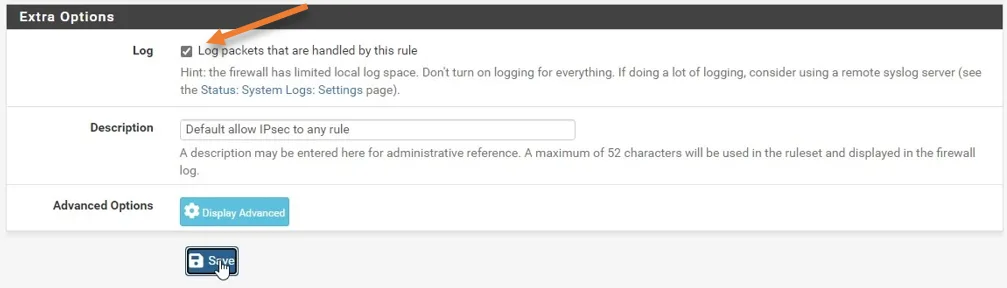
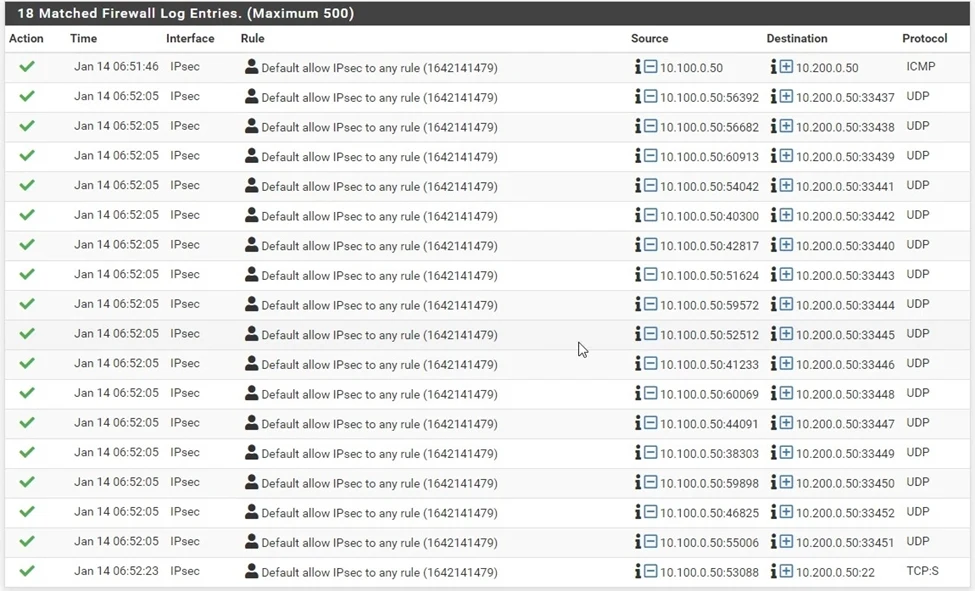
Check the IPsec logs on Pfsense.
Unlike Fortigate, in PFsense, you have to manually enable the logging on the policies.
Goto Firewall-> Rules->IPsec
You will see a log for the IPSec tunnel here. Click on the pencil icon to edit the rules.
Scroll down and check the Log Packets that are handled by this rule option and click on Save.
You may generate some more traffic. And if you go back to the PFSense firewall-> System logs-> Firewall
As you can see, the traffic between the pfsense and the fortigate Firewall.
We have successfully configured the IPsec tunnel between fortigate and pfsense firewall. We also confirmed the traffic is going through the tunnel and each host on the LAN side can communicate over the tunnel. This kind of setup will be helpful when you have a fortigate firewall in one of the sites and pfsense on the other side.
Lim
Sunday 27th of April 2025
What version of pfsense and fortigate is that ?