When you wanted to build and practice Paloalto lab, you have got multiple options.
You could try physical gears if you can afford one, else virtualize them.
In this blog, we will deploy the Paloalto firewall in gns3 with management IP and one public-facing interface connecting to the internet.
The Palo alto firewall works perfectly fine on the GNS3 environment. I have done multiple POC labs in GNS3 with it. One drawback is that without a license, you won’t be able to see traffic going across using the monitor function, also the dynamic updates. however, you should be able to get started and do many configurations that work fine.
I have created a beginners lab in GNS3, you can check them out here once you have set up the Palo alto in GNS3.
When you install the Paloalto in gns3 for the first time, certain things may not work well. Hopefully, we will close all those gaps and get you up and running in this lab guide and save you a lot of frustration and time.
Read also;
- Palo Alto Firewall Lab Setup-Allow Inside Users To The Internet
- How To Install Palo alto In VMware Workstation?
- How to Setup IPsec Tunnel between Paloalto and PFsense?
- How To Configure Palo Alto Site To Site VPN Using IPsec?
- How to Setup IPsec Tunnel between Paloalto and PFsense?
Before you start, there are few prerequisites for this lab
You need to have,
- Latest GNS3 software
- Palo alto qcow2 image – You can get the file here
Note: To get the Palo-alto image, you must have a service agreement with Paloalto networks.
If you don’t have a Palo alto agreement then google will be your best friend 🙂
Objective
We will integrate the Palo alto firewall with the GNS3, and set up the management interface. Access the firewall GUI from the local machine. After that, we will plugin the internet link and configure the outside untrusted network.
After we complete the above, you can jump to part2 of the lab Palo Alto Firewall Lab Setup-Allow Inside Users To The Internet.
Steps to install Palo alto in GNS3.
- Install Palo Alto firewall VM in Gns3.
- Change the network interface type.
- Configure the CPU
- Login to the Palalto CLI.
- Configuration of Paloalto management interface.
- Accessing Paloalto management GUI in Gns3.
- Enable internet access on the GNS3.
- Connect the Palo Alto to the internet
- Configure an internet IP address for the firewall outside interface.
Troubleshooting-tip - Validate the changes.
1. Install Palo Alto firewall VM in Gns3.
Let’s go ahead and deploy the Palo alto firewall in GNS3.
Open Gns3 and Click on security devices.
And click on the New template at the bottom.
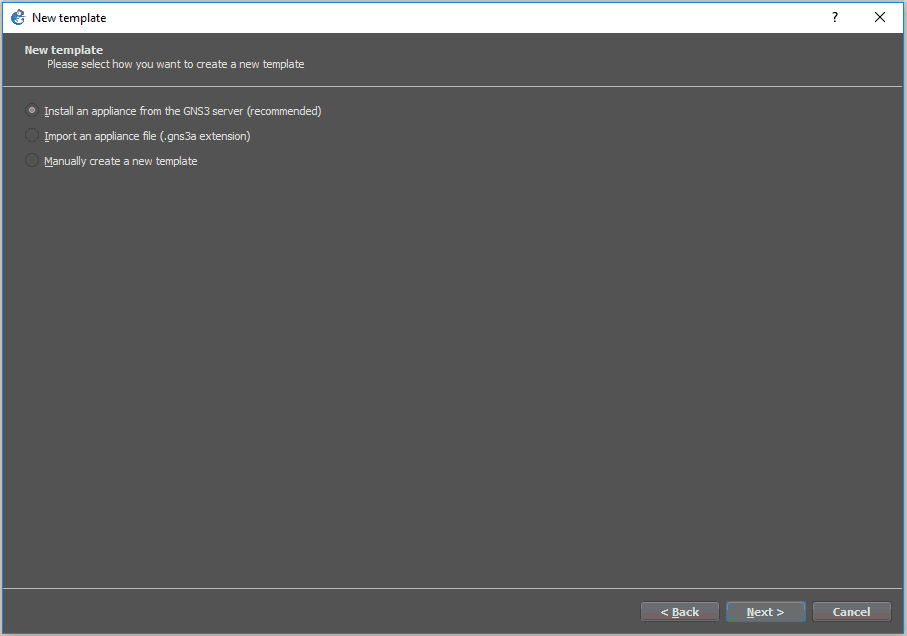
In the new template wizard, select install an appliance from the GNS3 server, and click next.
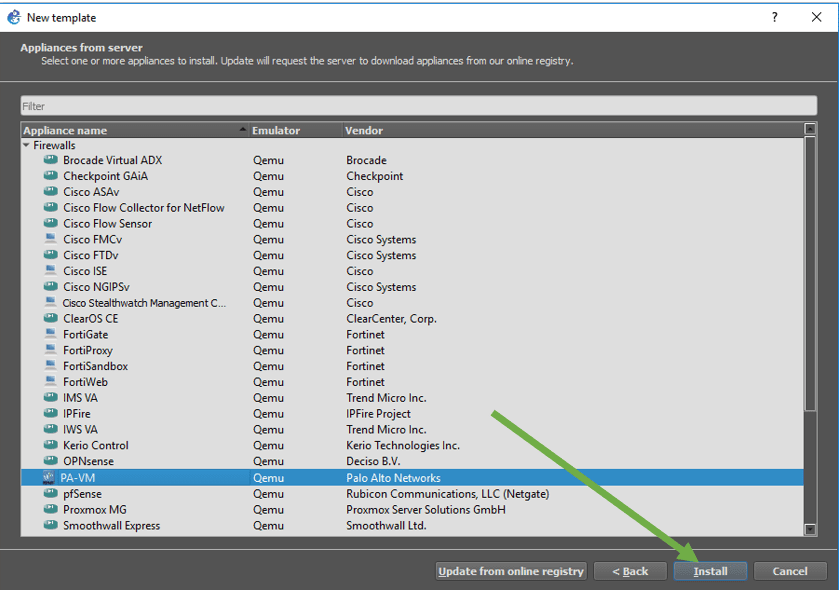
On the next screen, expand the firewall and select PA-VM (which represents Palo alto firewall) from the list and click install.
You will get a new pop-up window that says Install PA-VM appliance.
Install the appliance on a remote server, if you are using a remote server. As I am using the GNS3 as a remote server, I can choose this one.
OR
Select the option which says Install the appliance on the GNS3 VM (recommended) If you are using GNS3VM on the Vmware workstation.
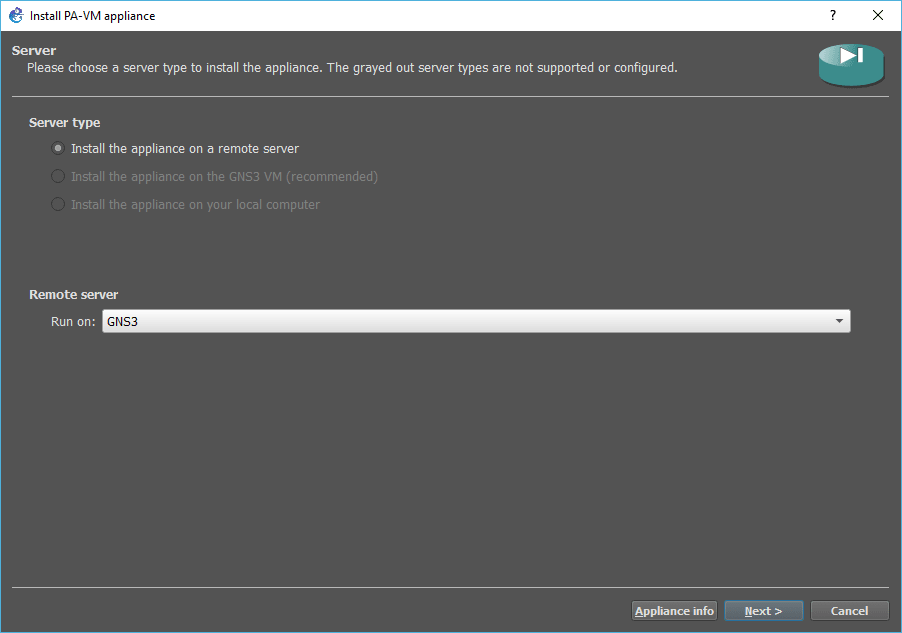
Once you select the option, click next.
If you are unfamiliar with the above options, then don’t worry. I have created a step-by-step guide on installing gns3 in your machine here.
Click next again on the Qemu binary window.
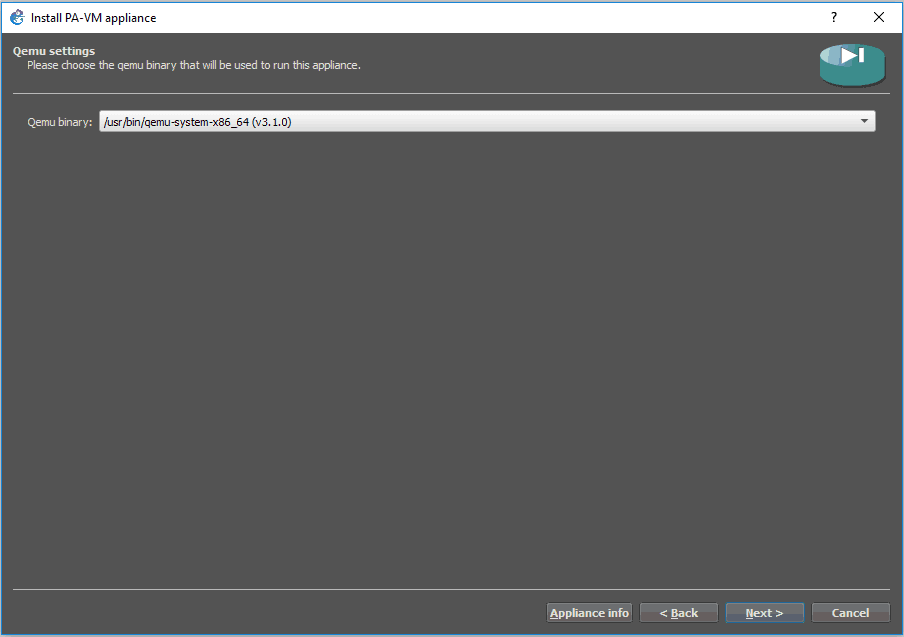
At the time of this writing, currently, the gns3 supports Paloalto version 10.0.0, however, the version that I have is 9.0.4. If you have a version that is not listed here, you may check the option Allow custom files and and click on New version, in my case that is not required as the version that I have is already listed there.
- Choose the disired version.
Note: Don’t worry about the VMDK extension, though we have a qcow2 file, it would work just fine. - Click on Import option down below to import the image to the gns3.
The import will take some time. - After imported, you will see the status as Ready to install click on Install.
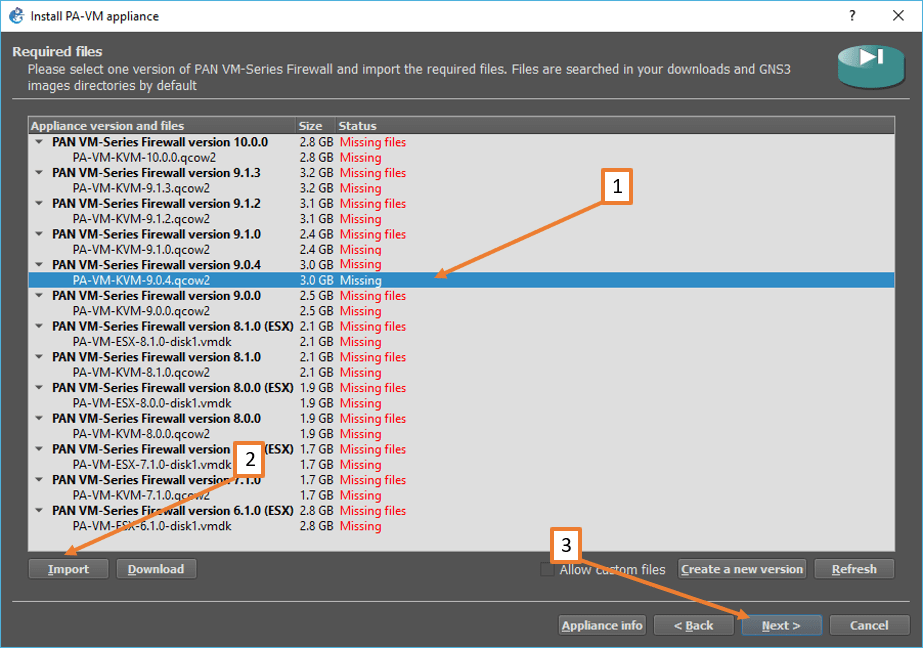
The properties of the Paloalto VM look like below. This window tells you about the default admin credentials and basic configuration on setting up the management interface and clicking on Finish on this screen.
You will be notified as a pop-up that the Paloalto version has been installed successfully.
You will now be able to see the firewall added under the security devices, like below.
2. Change the network interface type.
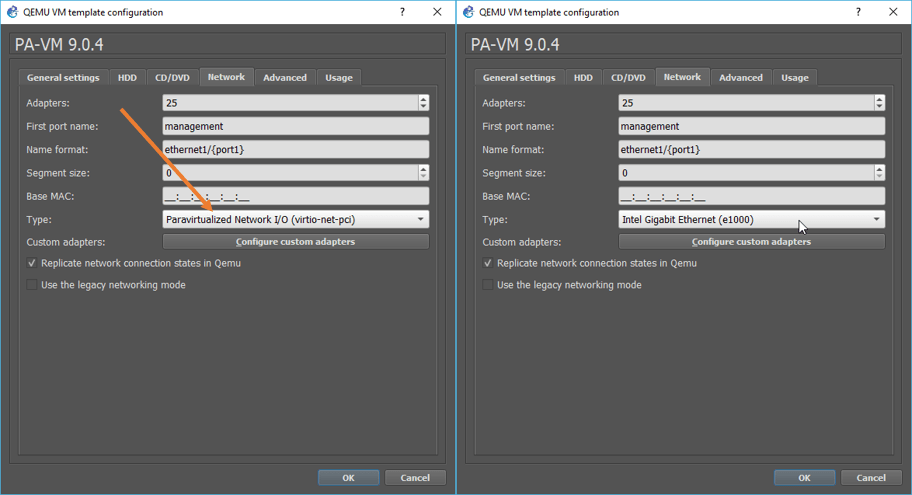
By default, the Palo firewall installed with the interface Type as Paravirtualized network I/O. You will have to change that as well.
This step is crucial. If you don’t change, you can only use the management side, not any other zone interfaces.
To change the network interface type, right-click on the Palo alto device that you have just installed and click on the Network tab, you should be able to see it is by default selected as Paravirtualised network I/O, click on the drop-down list, and choose Intel Gigabit Ethernet (e1000)
3. Configure the CPU
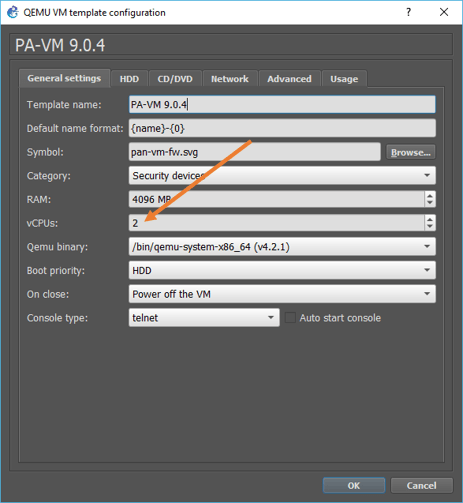
The Palo alto firewall would work just fine, with one CPU. However, to get a good performance, you are required to change the CPU to two.
In the same VM configuration window, click on General settings.
Change the CPU value to two, and click on OK.
4. Login to the Palalto CLI.
Alright, you have now successfully installed the firewall. Lets go ahead start the network configuration.
Drag and drop the firewall to the work area, right-click on the firewall, and power it on by clicking start.
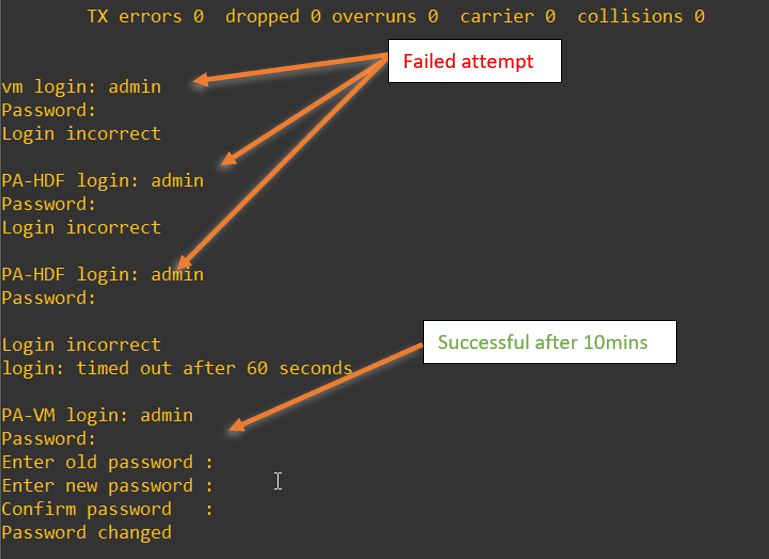
Double click on the device to open the console, and on the PaloAlto VM console, enter the username as admin and the password as admin.
Note: Once powered on, you have to wait for some time as the booting of the VM would take about 5-10 minutes. During this time, if you try to log in to the device, It will end up throwing an error that says ‘login incorrect’, which is expected..
If you are using Palo alto version 9 and above, when you try to log in with the default credentials, it would ask you to change the password right away. if you have the older version, you can still continue with the default credentials.
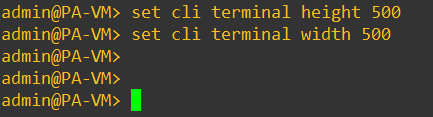
Change the terminal length on the Console.
There are chances on the CLI with default terminal settings when you try to get the output on the terminal. It doesn’t show the output properly on the screen.
To fix that, you will need to change the terminal length on the CLI screen. Double click on the CLI and adjust the terminal height and width with the below command.
set cli terminal height 500 set cli terminal width 500
set the terminal height and width as mentioned above.
5. Configuration of Paloalto management interface.
We were able to access the CLI, how about the GUI?
Most of the configurations that we perform are on the GUI, so to access the GUI, you will have to configure the Management interface IP.
To configure the management IP address of the firewall you can use the below command.
Here I am using the IP address 10.1.1.1. Which is part of the same subnet that we are going to use for the Virtual Adapter VMnet5.
My virtual adapter will have IP address 10.1.1.15 after the configuration, which we are going to perform next.
configure set deviceconfig system type static set deviceconfig system ip-address 10.1.1.1 netmask 255.255.255.0 commit exit
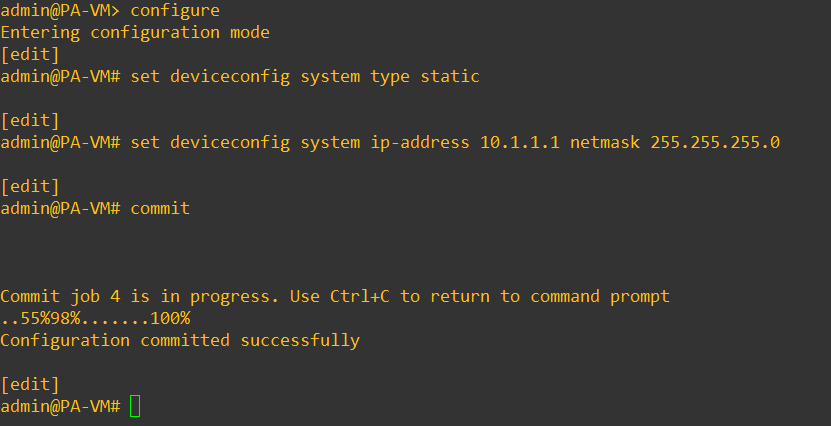
Exit out of the configuration mode by typing the command exit.
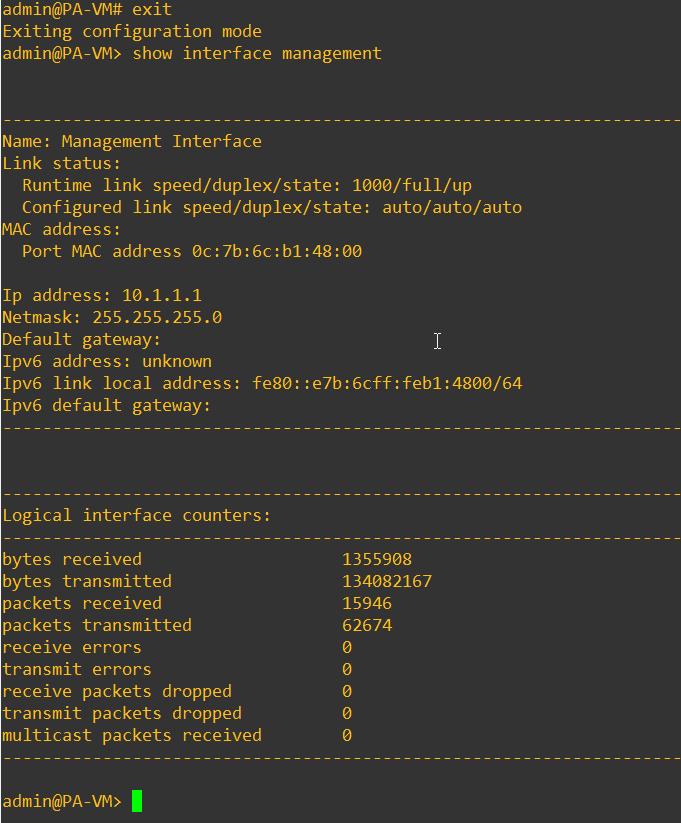
You may verify the IP address configuration by entering the command show interface management as you can see the management IP address of the Paloalto firewall now configured.
6. Accessing Paloalto GUI from Local machine.
I have tried in the past to access GUI with webterm and also with built-in firefox browser, but the performance with those clients was not good. so I recommend you choose the local machine option.
Let’s go ahead and configure a VMnet5 for that purpose.
Note: For the steps below, you need to have VMware Workstation installed on your machine, You don’t need to have a license. The trial license would work just fine. The idea here is to use the VMware workstation to manage the virtual adapters in GNS3.
You can go ahead and download and install VMware workstation pro.
You can click here to learn more about How To Connect GNS3 Devices To The Local Machine?
Add the Virtual adapter – VMnet5.
Start GNS3 and click on edit – preferences.
In the preferences pop up, click on VMware and click on the Advanced local settings.
In the managed VMnet interfaces select VMnet5 to VMnet5, then click on Configure.
That would create the VMnet5 virtual adapter on your machine.
Configure the VMnet5 IP address.
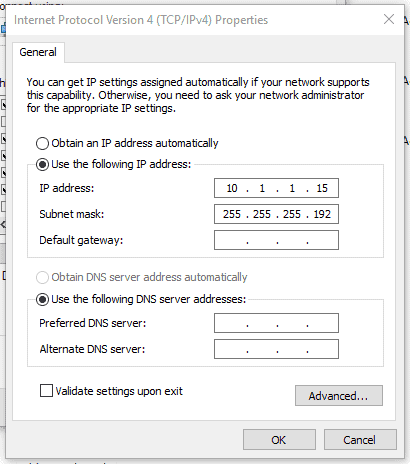
Go to Start – Run and type ncpa.cpl , which would open up all the interface configuration you have.
Right-click on the VMnet5 and click on Properties.
Double click on Internet protocol version 4 (TCP/IPv4). Enter the IP address and its subnet masks like below. I am configuring the IP address as 10.1.1.15 and subnet mask 255.255.255.192, then click on OK.
Configure the Cloud with VMnet5.
Add a cloud to the topology, and Right-click, and click on configure on the cloud, check the option which says Show special Ethernet interfaces.
Then select VMnet5 and click on Add, and delete all other Ethernet interfaces and click on OK.
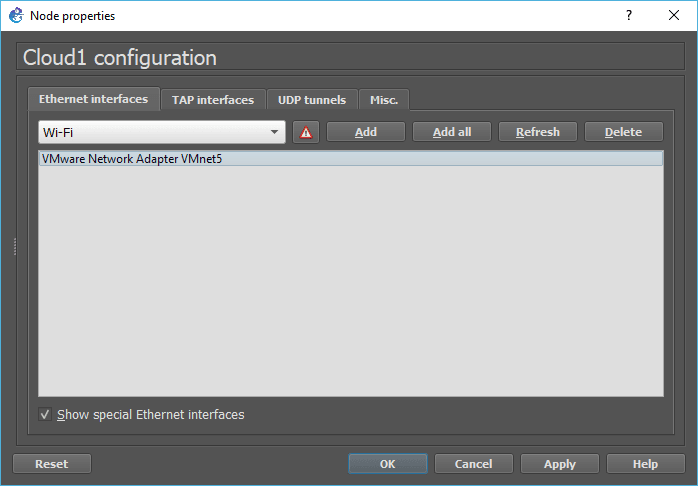
Connect the cloud to the Paloalto management interface.
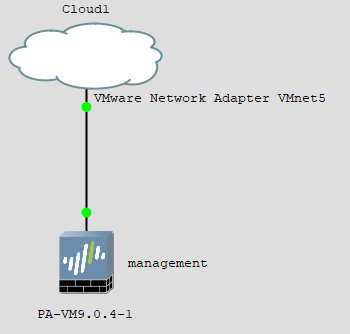
Try to ping the firewall IP from your local machine, and you should be able to receive a response.
C:\Users\saif>ping 10.1.1.1
Pinging 10.1.1.1 with 32 bytes of data:
Reply from 10.1.1.1: bytes=32 time=56ms TTL=64
Reply from 10.1.1.1: bytes=32 time=77ms TTL=64
Reply from 10.1.1.1: bytes=32 time=96ms TTL=64
Reply from 10.1.1.1: bytes=32 time=14ms TTL=64
Ping statistics for 10.1.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 14ms, Maximum = 96ms, Average = 60ms
C:\Users\saif>Finally, Access the Palo Alto GUI in GNS3
Try to access the management IP address of the Paloalto now from your local machine.
Ignore the security warning, and you should be able to see the Palo-Alto GUI window like below.

You may log in with the username admin, and password that we changed using the CLI.
As you can see below, we have successfully installed Palo alto VM version 9 in gns3.
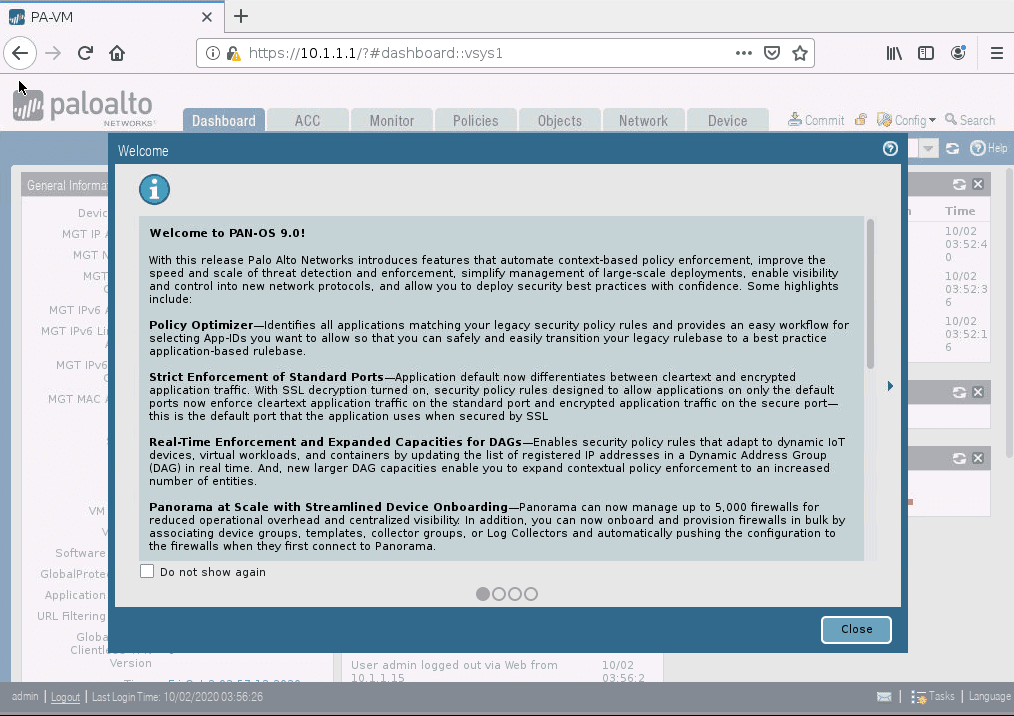
7. Enable internet access on the GNS3.
We have to now connect the firewall to the internet, How are we going to connect Paloalto to the internet?
Just like we configured the management interface, we can use the virtual adapter for sharing the internet access as well. Lets go ahead and use VMnet2 for internet sharing.
Configure virtual adapter – VMnet2.
You may click on Edit – preferences in gns3.
In the preferences window, click on VMware and go to Advanced local settings.
In the managed VMnet interfaces, select vmnet2 to vmnet2 and click on Configure.
It will create the VMnet2 virtual adapter on your local machine.
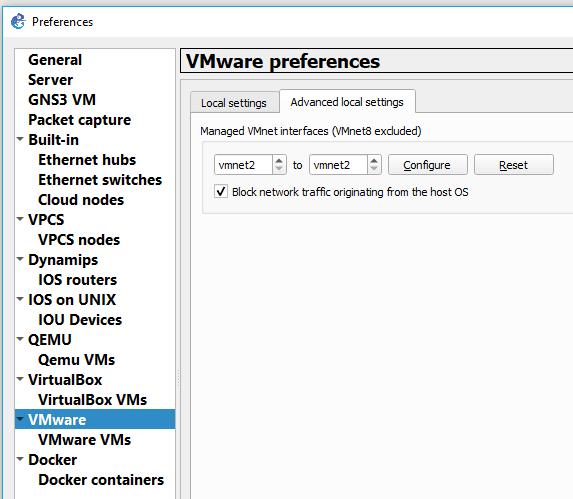
Configure the VMnet2 adapter to share internet access
You just installed the VMnet2 adapter on your machine, let’s go ahead now and configure it to use the internet.
Go to Start, then Run and type ncpa.cpl and click OK. That will open the virtual adapter configuration on your windows machine.
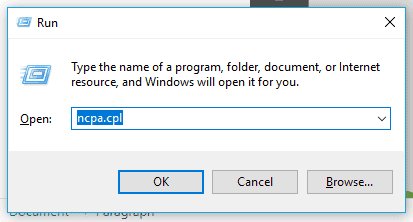
You may right-click either the ethernet or wireless adapter, depends on where you have connected to the internet.
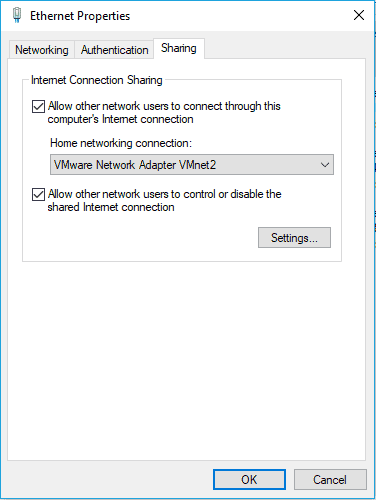
And click on properties. Since I am using a wired connection for the internet, I have right-clicked on it and check the option which says Allow other network users to connect through this computer internet connection. Then select VMnet2 from the dropdown and click on OK.
As soon as you share the internet access, the VMnet2 adapter would start to use the IP address 192.168.137.0/24
Configure the GNS3 Cloud to connect to the internet.
It is very unlikely that you will use a public IP address in gns3 and route traffic. By enabling the internet in gns3, you are going to get an IP address from the private IP range 192.168.137.0/24.
Add a second cloud to the topology. You will get a prompt to choose a server. Remember that you configured the VMnet2 on your local machine, so select the local machine as the server and click on OK. You may now right-click on the Cloud and click on configure.
The cloud configuration windows would show you the list of physical interfaces that are present in the machine.
In my machine, I could see three Ethernet interfaces. I will delete all three and check the option down below, which says Show special Ethernet interfaces and choose VMnet2 from the drop-down and click on Add and click on OK.
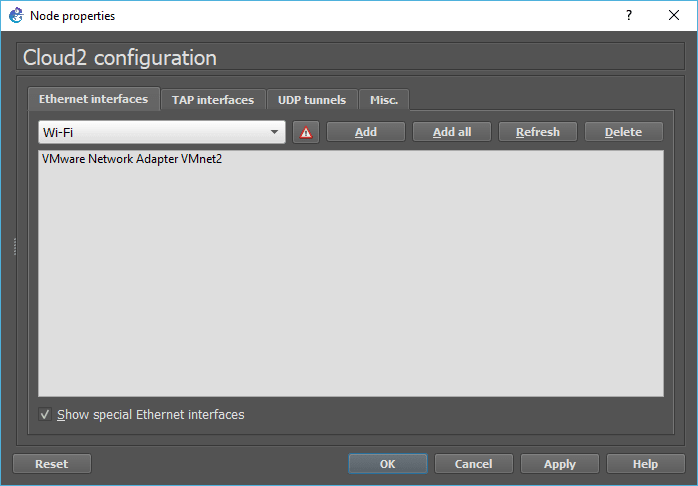
8. Connect the Palo Alto to the internet.
Our second cloud is ready to share the internet access, connect the cloud to the Paloalto ethernet1/1 interface.
Once connected, the topology would look like below. The cloud on the top provides internet access to the Firewall and the bottom one for the management interface.
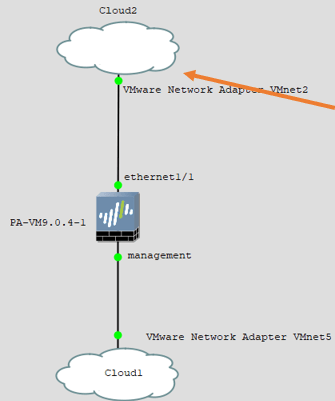
9. Configure an internet IP address for the firewall outside interface.
We are just configuring the outside interface with IP to test whether the internet IP assignment is working or not and the local machine is able to share the internet access with Paloalto.
- Open the Paloalto web GUI.
- Goto network, then click on interfaces.
- Click on ethernet 1/1
- Change the interface type to Layer3 and choose the router as default.
- In the Security Zone, click on New zone, the zone creation pop up will open.
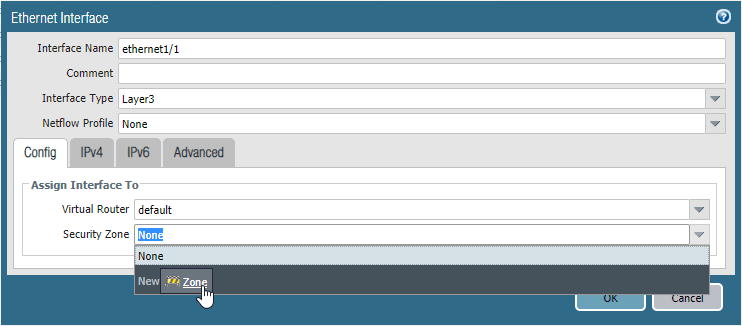
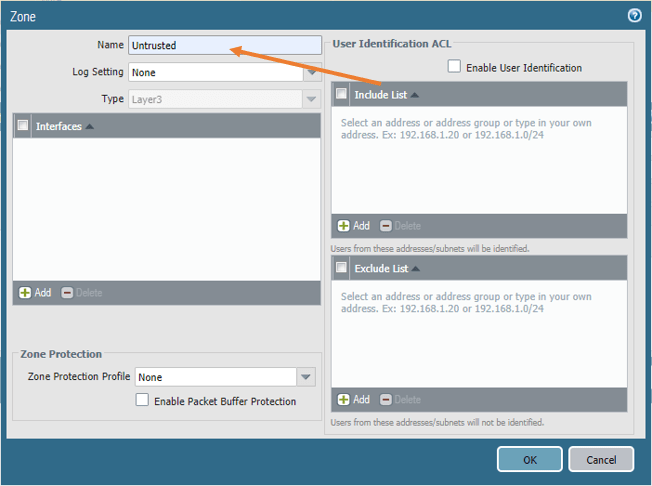
- In the zone createion window, Name the zone as Untrusted and click on Ok
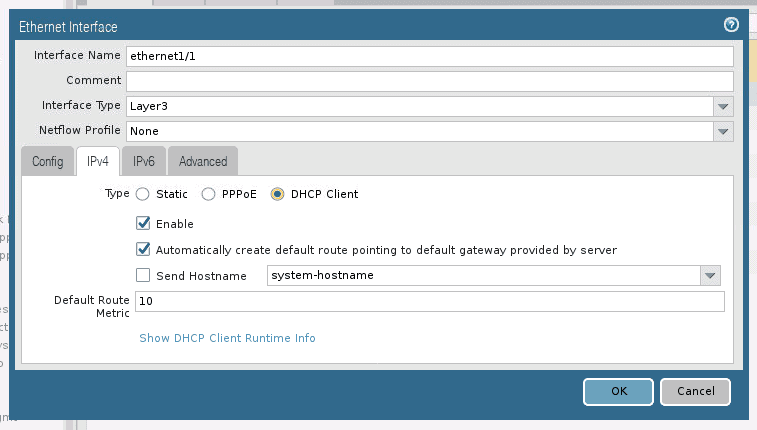
Click on IPv4, and check the option DHCP client and click on OK.
Allow the ping on the outside interface.
During the troubleshooting, it is recommended to have ICMP enabled on the outside interfaces, Click on advanced, and click on Management Profile drop down.
Click on New Management Profile.
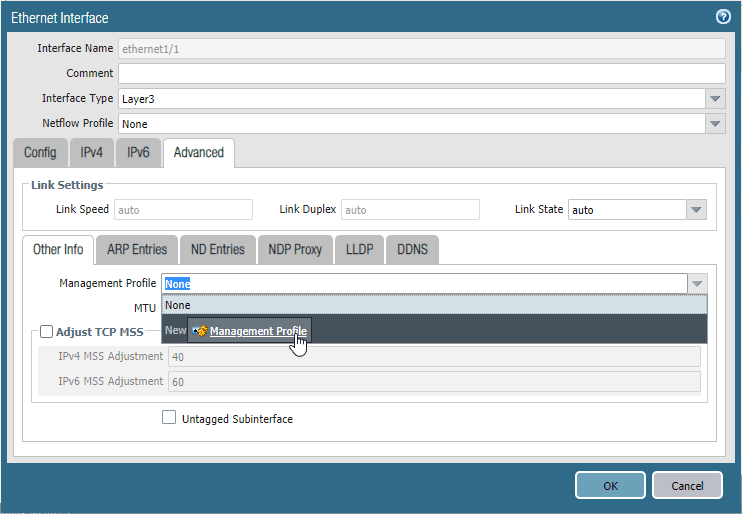
The management profile window will now open. Name the profile and check the option Ping and click on OK.
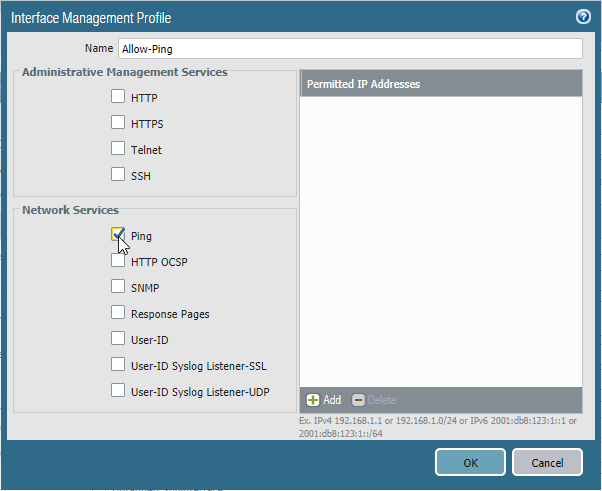
Commit the changes.
We made some changes, to reflect the changes, click on the commit button on the top right corner.
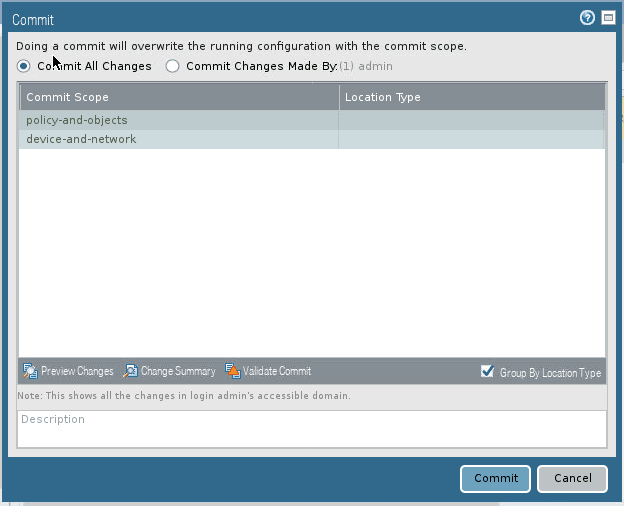
10. Validate the changes.
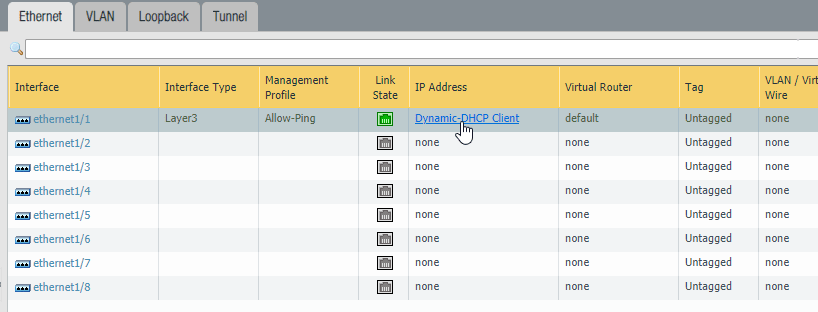
After you committed the changes, you should be able to see the interface with the green color that indicates the interface is physically connected and it is up.
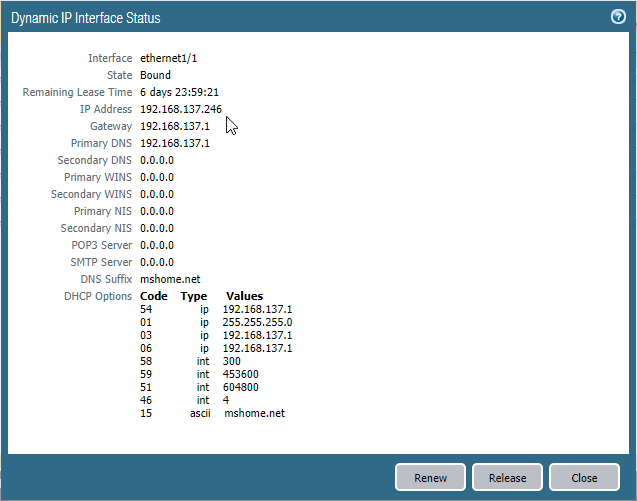
To see the IP address that is given by the DHCP, you may click on the Dynamic-DHCP Client.
You should get the IP address details in the Dynamic IP interface status window, and my IP address is 192.168.137.246.
Note: If you are not getting the IP address automatically, which means you have not configured the internet sharing properly, validate step7 again.
We have successfully installed the Palo alto firewall in GNS3. In case if you have run into any issues I have added some troubleshooting steps below.
Now we need to also see how you can allow the inside users to the internet, which covered here in more details.
Troubleshooting tip:
There are times your Palo alto firewall cannot communicate with the host machine, maybe after you left the PC for idle and it went to sleep. And this is how you can troubleshoot the issue.
- Make sure the local machine firewall or antivirus software is not blocking the network coming out of gns3. To test that, you may disable the antivirus software on your local PC and reopen the topology again.
If disable did the trick, you may go to the antivirus software rules and allow the subnets that we cannot access. - If that didn’t fix the issue, then follow the below.
- You can disconnect the link between the Paloalto firewall and the cloud.
- In GNS3 goto edit->preferences->VMware->Advanced settings.
On the interfaces, select the interface that you have issues with, for example, VMnet5 to VMnet5, and then click on configure.
Gns3 will reset the interface to its default.
- You may close the gns3 and go back to the network adapter configuration on your local machine and reconfigure the subnet that you wanted to use, for example, 10.1.1.15/24
- Open Gns3 and the topology that you were working, connect the cloud to the firewall again, it should fix the issue, and you should be able to access the firewall GUI from your local machine.
