When you spin up a Ubuntu instance in AWS EC2 you will be able to log in using the private key that you have downloaded prior to the deployment. Which we have seen in my last blog on how to spin up Ubuntu-server on an EC2 environment.
By default login to the instance using the username and password is disabled. And using the key pair is the recommended and secure method from the AWS, so use the following method only if it is necessary.
In this blog, we are going to see how you can log in to the Ubuntu instance using the username and password. We will also tighten the security that way only you will be allowed to login rest all will be blocked.
1. Spin up a Ubuntu instance.
You may already have the Ubuntu server instance running on your EC2, if not follow the step-by-step guide here to see how you can spin up an instance.
2. Secure the SSH access.
If you have followed my previous guide, you must have already done this step as well.
By default, when you choose the default security group while creating the EC2 instance, it will have ssh access enabled across the internet, we are going to restrict the access to only your public IP, which means only you can log in to the Ubuntu server rest all will be blocked.
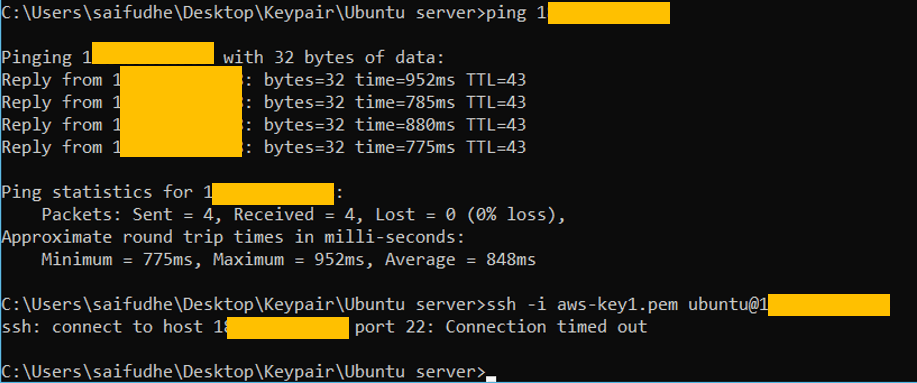
You can see below, I am able to ping but the ssh is timed out. Because I have allowed only the ICMP access, which we will see in few seconds.
- Find out your Public IP.
If you are at home following this guide, you most likely will have dynamic Public IP from the internet. So you can click here to know what is your Public IP.
I have static IP that I got from my ISP, which is dedicated to me and will never change. And all the enterprise networks will have a static address associated with them.
Make a note of your Public IP.
- Harden the security group.
Goto EC2–> Network &Security–> Security Groups.
Here you will see the list of the security groups that is available in your VPC environment, choose the one that is associated with your Ubuntu machine.
As I said before, I have only ICMP enabled for this host from everywhere, which means I can ping the host anywhere across the internet but the rest of the traffic will be blocked.
And click on Edit inbound rules.
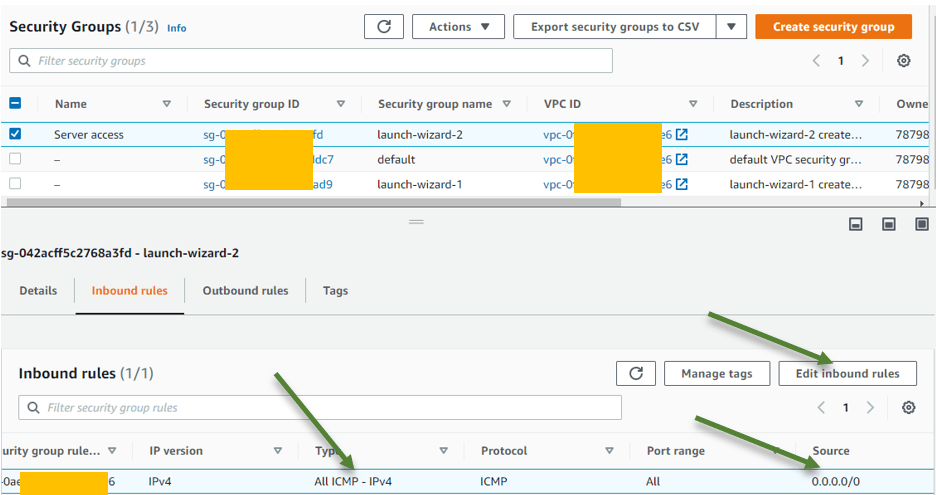
What many people will do when the SSH doesn’t work is that they will enable ssh from anywhere which is not a good security practice.
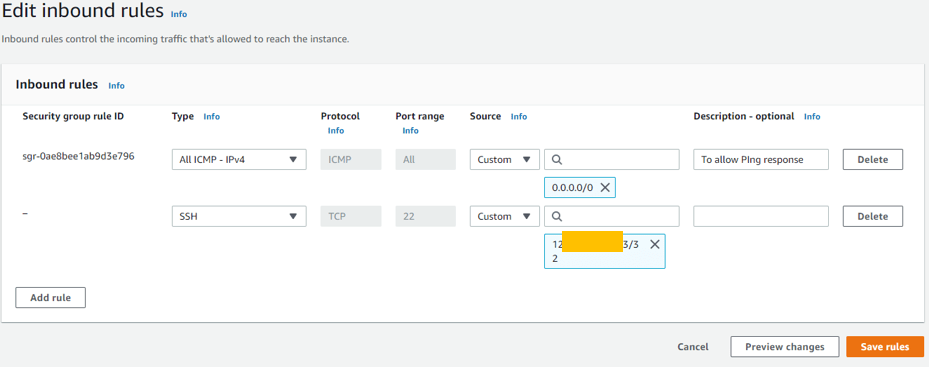
- Click on Add rules.
Under the source, IP field, add your public IP address and save the rules.
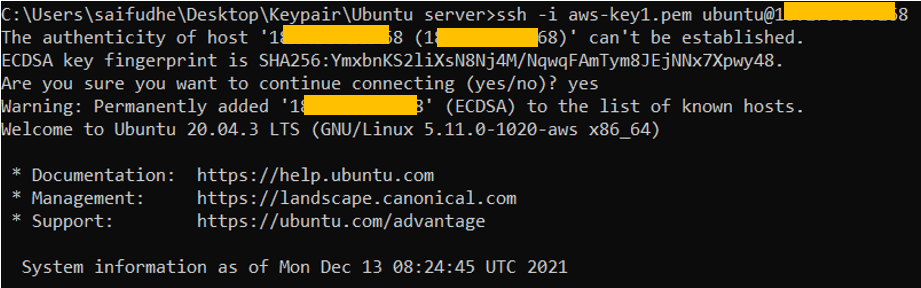
Try to SSH into the Ubuntu machine now.
As you can see I can ssh into the machine now. Rest all public IP address will be blocked.
3. Enable the login access to Ubuntu using username and password.
Login with the password is blocked by default on the Amazon linux instances, hence we will need to make changes to the ubuntu ssh configuration then you should be able to login.
As you can see, when I tried with just the username my access was denied.
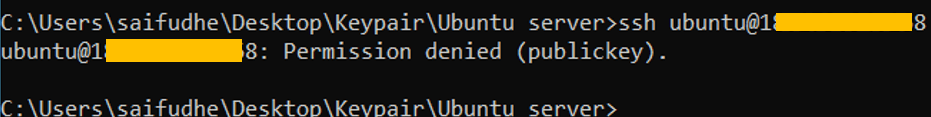
4. Enable password authentication.
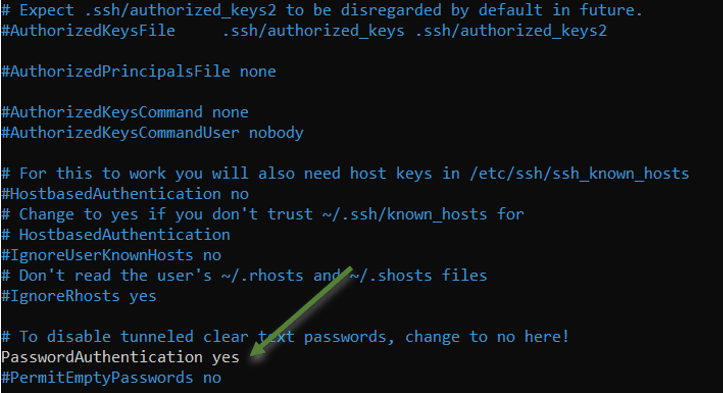
Open /etc/ssh/sshd_config and set passwordauthentication to Yes.
sudo nano /etc/ssh/sshd_config
Scroll down and in PasswordAuthentication change from No to Yes.
- Restart the ssh service.
In order for the changes on the SSH config to affect you will have to restart the ssh service. Type the command below to restart the ssh service on ubuntu.
sudo service sshd restart
or
sudo systemctl restart sshd
5. Set the password for the Ubuntu user.
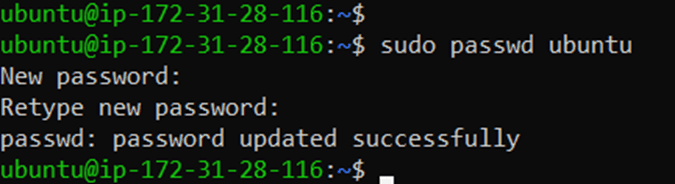
Now that we have enabled the password authentication through ssh, you will have to set the password for the ubuntu user as by default the password is not been set.
To set the password type the command below.
sudo passwd ubuntu
it will prompt you to create a new password for the user Ubuntu.
As you can see I have set the password successfully.
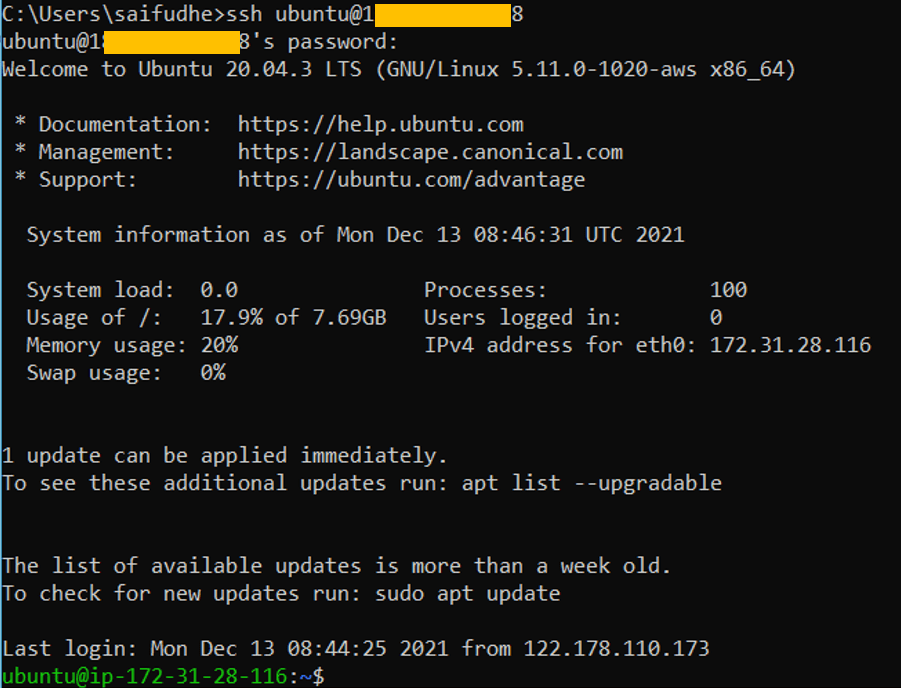
6. Login to the Ubuntu instance with username and password.
Login to the Ubuntu host with just a username, if you have done everything correctly until this point you will get a prompt for authentication and you should be able to authenticate just fine.
Conclusion :
With the steps above, you will be able to log in to the Ubuntu machine using SSH credentials instead of the keypair. And we also hardened the security by allowing only your specific IP to the SSH access.
There is no doubt, in production you must allow ssh access to specific IP, and if you are allowing ssh access using the username and password you must allow the ssh access to specific IP be it in production or a test environment, cos on the internet the bad guys will keep doing the brute force attack to the AWS public IP’s, so in case if you have used bad password they will be able to get in if you have allowed ssh from anywhere.
Is dynamic IP is secure to use as a source: The static IP is secure, and most of the dynamic IP deployment ISP use something called CGN – Carrier-grade Natting, meaning your dynamic public IP used by multiple subscribers on the internet, that will be for another discussion.