In a big network environment where you have hundreds or even thousands of devices connected, anything can go wrong at any point in time. So as a network or system engineer it’s your responsibility to make sure that all the systems are up and working at all times. In case anything goes wrong you need to find out what is going on.
The question now is, how do we get to know there is something wrong with the environment proactively rather than reactively. That way you will be alerted well in advance when something is not right, instead of customers who report the issue saying they are not able to access certain resources on the network.
What is SNMP used for?
Well, you now know that we need to proactively monitor the network devices somehow, so how do we achieve that.
Simple Network Management Protocol is a standard network management protocol defined in RFC 3416 is used to monitor and maintain the network equipment. There will be two machines talking to each other, first is the SNMP agent which listens to the SNMP services. The second is sthe management server, which polls the SNMP hosts on the network.
You can use the Simple Network Management Protocol (SNMP) to monitor and manage the health of your network devices. It works on the Application layer and exchange network management information between the manager and the agent.
SNMP Polling.
Once you have the SNMP configured and set up on a network device. The SNMP manager can poll the SNMP agent on port 161/UDP on a different interval that is set by the administrator and get the device health status.
SNMP Traps.
Instead of SNMP manager polling the network devices on a frequent interval and identify the issue. The agent can also send a Trap over port 162/UDP in the event if something goes wrong.
For example, on a network device, When the network utilization or the temperature of the network devices gets high, the SNMP trap can be sent at this point by a device to the manager.
If it is a server, then the memory, hard disk, or CPU utilization alerts, and so on.
On a normal network environment, you can find the SNMP manager configured with a mix of polling as well as traps.
SNMP configuration on network devices.
In some of the operating systems, you would require the SNMP package to be installed before you start the configuration and monitoring them. However, network devices such as routers and switches already have the SNMP feature pre-installed and it can work out of the box. Of course, you need to run some commands to activate them.
Must read:
Install SNMP on a Linux Redhat or Centos Machine.
Install SNMP on an Ubuntu machine.
What are the different SNMP versions?
When the SNMP protocol first came out back in 1988 it was not so perfect, as a result, multiple versions of SNMP protocols were announced later. The version of SNMP are;
SNMPv1
It is the first version of SNMP and it uses community string to communicate with the SNMP manager. But it was lacking security as at the beginning of network development, no one thought they require security on the network.
SNMPv2c
Though there was multiple version of SNMPv2 came out after version1, only SNMPv2c became more popular and it is the SNMP version widely used as on today. It was more fine-tuned and robust. But it is still using the community string to communicate.
What is SNMP community string?
Okay, I have been talking about community string so much, what are they?
The SNMP community string that acts as a password on the SNMP version 1 and 2 between the SNMP manager and the agent.
A community string can be configured on the SNMP manager and the same string has to be configured on the agent to communicate with the Manager. By default, most of the network equipment uses the default community string public, you should never use the default one instead you should use something complex.
If the community string doesn’t match on both sides the manager and the agent won’t be able to communicate.
You can have a community string that is read-only or read-write.
As the name suggests the read-only community string can only view the information inside the system, whereas the read-write can make the changes on the device. There is some network management software that can use the read-write community string to make changes on the network equipment as well.
SNMPv3.
The SNMPv3 was developed with security in mind, the configuration is a little different as compared to version 2. As the SNMPv3 doesn’t use community string and it uses username and password to authenticate. Unlike other versions of SNMP’s. SNMP v3 provides authentication, privacy, and encryption.
But it can still be configured as SNMPv2 with no authentication, privacy, and encryption.
SNMP version comparison chart
Below is the chart that explains the different SNMP Security Models on a different version of SNMP.
Auth = authentication
Priv = Privacy.
| Model | Level | Authentication | Encryption |
| Version1 | noAuthNoPriv | Community string | No |
| Version2c | noAuthNoPriv | Community string | No |
| Version 3 | noAuthNoPriv | Username | No |
| Version 3 | authNoPriv | MD5 or SHA | No |
| Version 3 | authPriv | MD5 or SHA | Yes |
Different components of SNMP.
Now you know the SNMP can identify what’s going on in your environment and the administrator can take action appropriately, so how does SNMP monitor the network.
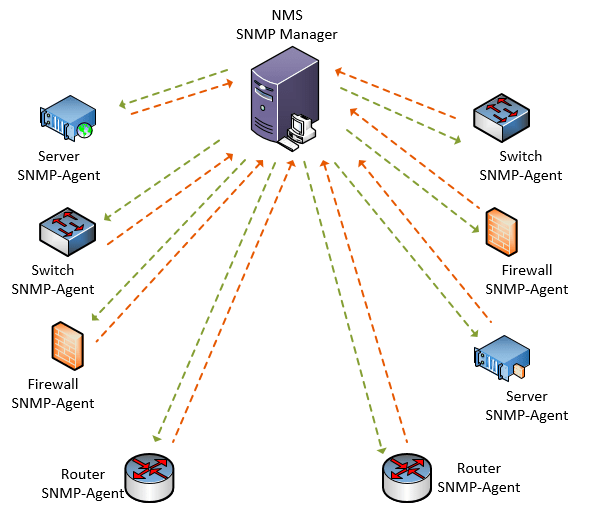
There are two components in the SNMP that can help you to accomplish this. The first one is the SNMP manager and the second one is the SNMP agent.
SNMP Manager.
The SNMP manager is also known as NMS (network management station), is the place where you put the SNMP management software. It can be any network monitoring solutions such as Nagios, SolarWinds, and so on. The administrator can set an interval for the SNMP manager to poll the devices on the network. The polling happens with the SNMP message SNMP Get.
And during the polling time when the SNMP manager found there is an issue it can alert the device administrator.
SNMP Agent.
The SNMP agent is the software or service that is running on the network devices that you would like to monitor. The SNMP manager is always connected to the SNMP agents using a community string if it is SNMPv1 or V2c, username and password if it is SNMPv3.
How SNMP works?
The SNMP agent will have something called Management Information Base (MIB) which is a hierarchical database present locally on the SNMP agent. It contains the name data type and the OID.
The MIB values on a device may not be the same as other devices, especially different vendors. Because of this, when you implement any SNMP monitoring solution it is recommended you go to the vendors support page to get the MIB information. However, some of the NMS software’s do have a default inbuilt MIB’s information for common network devices.
The OID that exists in MIB is a tree-like structure and each OID represents different values in a numeric format. You can have OID for CPU, Memory, Storage usage or network interface status, and so on.
When the status changes on the OID values, the SNMP agent can send the traps or inform the SNMP manager.
Which ports does SNMP use to function?
Like any other network protocol, SNMP does use port numbers to communicate over the network. There are two ports used by the SNMP devices. In which the SNMP manager talks to the SNMP agent over port 161, and if the SNMP agent is sending any traps or inform messages to the management server then it uses port 162.
It is recommended that you allow both the 161 and 162 port number on the host firewall in order for the communication to happen.
The configuration of the SNMP is not so difficult, I have covered a couple of blogs specific to SNMP in my blog. The reason why SNMPv2c is widely used because some of the NMS software don’t support SNMPv3. Hence the admins have configured as SNMPv2c in the beginning and never updated them. However, if you have the NMS on the latest version, the chances are it supports SNMPv3.
So, if you have to configure the SNMP on your environment and your NMS software does support version 3 then it is recommended to use the SNMPv3.