Yes, we are almost there to get everything up and run.!
I am building this lab for you guys and at the same time, writing this post, that way I hope everything would be accurate.
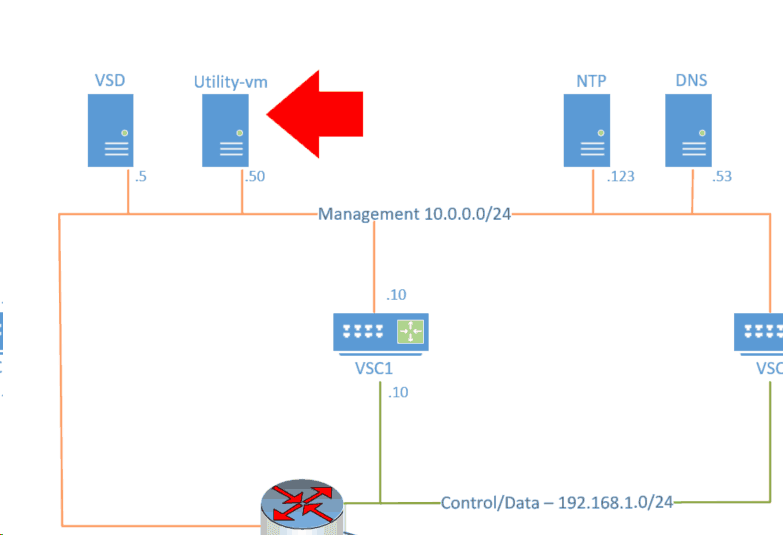
In this lab, we are going to install the Nuage proxy server, also known as nuage utility VM, so let’s get started.
Why Nuage SD-WAN Proxy?
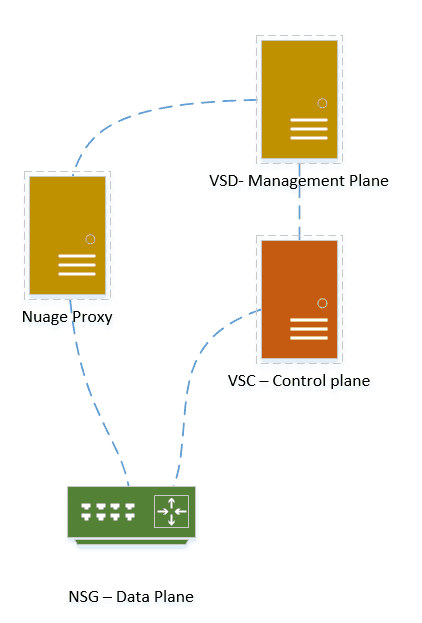
Nuage proxy is the last SD-WAN component that we are going to install in order for the SD-WAN to function.
In nuage SD-WAN, the NSG doesn’t talk to the VSD directly, as it’s not recommended to expose VSD to the public internet. Instead, we use a proxy between the VSD and the NSG.
Now when the new NSG is deployed on the site and wanted to bootstrap them, it would first send the request to Nuage proxy.
It also acts as a notification app for NSG.
Follow the steps below to install the nuage proxy component.
- Prerequisite
- Nuage SD-WAN Proxy installation steps.
- Nuage proxy configuration
- Installation of nuage proxy services.
- Enable nuage proxy services.
- Final verification in the nuage proxy
1. Prerequisites
- Nuage sample utility VM
In the software package from Nuage, the sample utility VM also included, and it is based on Linux and acts like a proxy server in the lab. Still, it’s not recommended to use utility VM in production. You should use F5 or other devices for this functionality. - The proxy server should connect to the management network, and the interface already created.
2. Nuage SD-WAN Proxy installation steps.
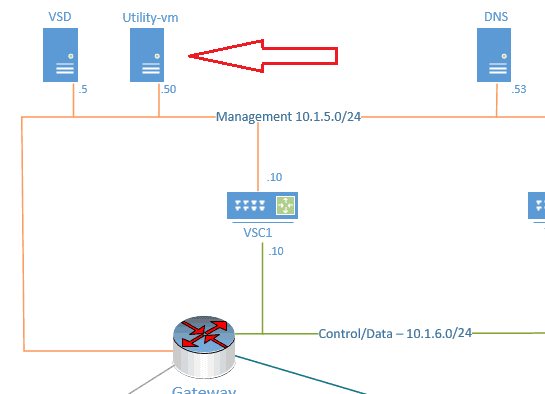
As you can see the nuage utility, VM is located on the management network and has an address of 10.1.5.50
The installation of the nuage proxy server follows the same process as VSD and VSC, you can either use XML or manually.
I am doing it manually for this proxy VM deployment.
Step 1. Create a folder called proxy in var/lib/libvirt/images folder
Step 2. move vns-util-5.2.2-16.qcow2 to the KVM host, var/lib/libvert/images/proxy location.
Step 3. Type virt-manager in terminal KVM virtualization manager would open.
- Click on Create a new virtual machine.
- Select the Import existing disk image and click forward.
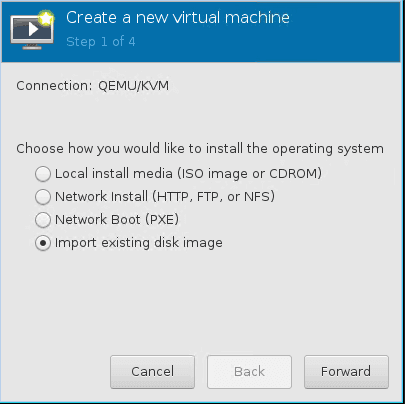
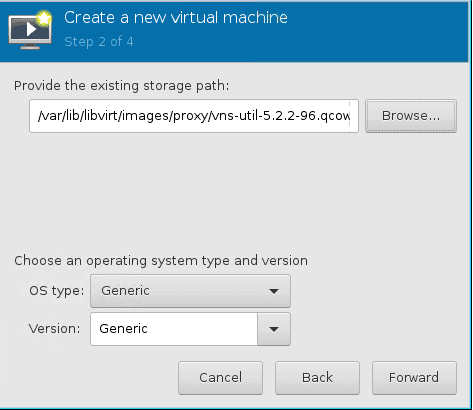
- Browse for the utility VM image and click forward.
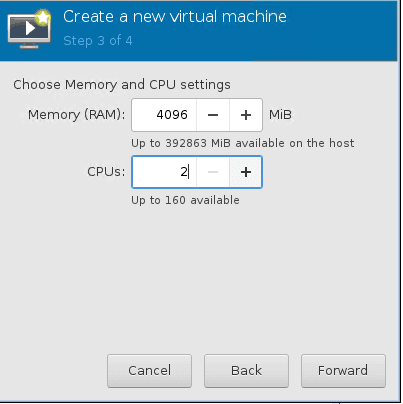
- Give 4gig Memory and 2 CPU.
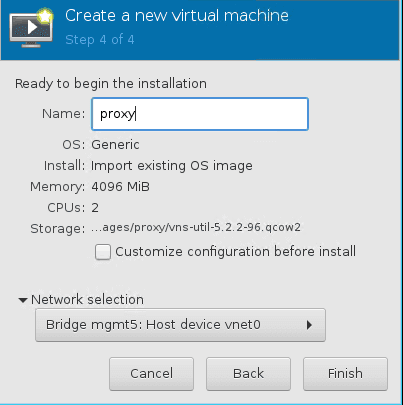
- Name the VM to proxy and select the management interface and click on the finish.
- Once the installation is over, login VM by using nuage proxy server credentials below.
root Alcateldc
3. Nuage proxy configuration.
Step 1. Proxy network configuration
Disable the cloud-init by entering the below command in nuage proxy VM. This is important; otherwise, next time when you reboot the VM, everything would be gone, such as nuage proxies network configuration and DNS configuration and so on. So let’s do that.
systemctl disable cloud-init systemctl disable cloud-init-local systemctl disable cloud-config systemctl disable cloud-final
- Assign the static IP address that we reserved for nuage PROXY, which is 10.1.5.50, as well as DNS configuration.
DEVICE=eth0 NM_CONTROLLED=no ONBOOT=yes TYPE=Ethernet BOOTPROTO=static IPADDR=10.1.5.50 GATEWAY=10.1.5.1 PREFIX=24 DNS1=10.1.5.53 DOMAIN=getlabsdone.com
- Restart the network service
service network restart
Step 2. Nuage Proxy Initial configurations
- Change the hostname
/etc/hostname proxy.getlabsdone.com
Note: Make sure this hostname is resolvable everywhere, VSD, VSC… Etc.
- Also, add the host entry in the /etc/hosts file.
10.1.5.50 proxy.getlabsdone.com
- Reboot the server
Step 3. Create the proxy user in VSD for the proxy server
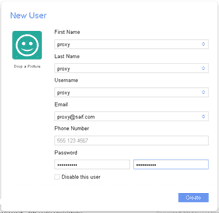
- Login to Nuage VSD Architect and click on platform configuration which is there on the top right corner,

- Click on setting and the user
- Click on the plus icon to create a user “proxy” under CSProot
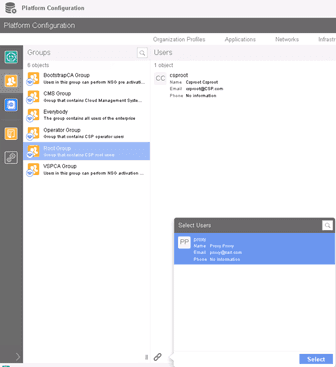
- Add the proxy user to Root groups.
Step 4. Install the certificate in the nuage proxy server
/opt/vsd/ejbca/deploy/certMgmt.sh -a generate -u proxy -c proxy -o csp -d proxy.example.com -f pem -t server -s root@<proxy IP>:/opt/proxy/config/keys/
- Change the value according to the lab and run this command in VSD.
/opt/vsd/ejbca/deploy/certMgmt.sh -a generate -u proxy -c proxy -o csp -d proxy.getlabsdone.com -f pem -t server -s [email protected]:/opt/proxy/config/keys/
- Now we have just installed the certificates in Proxy, you can verify by going to the below folder in the proxy server.
/opt/proxy/config/keys [root@proxy ~]# ls /opt/proxy/config/keys/ BootstrapCA.pem proxy-bootstrap-privatekey.pem proxy-bootstrap-cacertificate.pem proxy-CA.pem proxy-bootstrap-certificate.pem proxyCert.pem proxy-bootstrap-combined.pem proxy-Key.pem proxy-bootstrap.pem proxy.pem [root@proxy ~]
4. Installation of nuage proxy services.
To install the service, enter the below command in the nuage proxy server.
[root@proxy ~]# rpms/install.sh -x vsd.getlabsdone.com -u proxy.getlabsdone.com IPv4 Enabled Installing ... [ 801.792463] nf_conntrack version 0.5.0 (16384 buckets, 65536 max) [ 801.806252] ip6_tables: (C) 2000-2006 Netfilter Core Team [ 801.853992] Ebtables v2.0 registered [ 801.864702] Bridge firewalling registered running NotificationApp update config Updating cron Done Note: Forwarding request to 'systemctl enable httpd.service'. Created symlink from /etc/systemd/system/multi-user.target.wants/httpd.service to /usr/lib/systemd/system/httpd.service. Redirecting to /bin/systemctl restart httpd.service Note: Forwarding request to 'systemctl enable supervisord.service'. Created symlink from /etc/systemd/system/multi-user.target.wants/supervisord.service to /usr/lib/systemd/system/supervisord.service. Restarting supervisord (via systemctl): [ OK ] Note: Forwarding request to 'systemctl enable rsyslog.service'. Redirecting to /bin/systemctl restart rsyslog.service Note: Forwarding request to 'systemctl enable ntpd.service'. Created symlink from /etc/systemd/system/multi-user.target.wants/ntpd.service to /usr/lib/systemd/system/ntpd.service. Redirecting to /bin/systemctl restart ntpd.service [root@proxy ~]#
5. Enable nuage proxy services.
To Enable services by executing the following commands to start haproxy and supervisord (notification app)services, at the startup.
chkconfig haproxy on chkconfig supervisord on service haproxy restart service supervisord restart /opt/proxy/bin/restartServices.sh
Output
[root@proxy ~]# chkconfig haproxy on Note: Forwarding request to 'systemctl enable haproxy.service'. Created symlink from /etc/systemd/system/multi-user.target.wants/haproxy.service to /usr/lib/systemd/system/haproxy.service. [root@proxy ~]# chkconfig supervisord on Note: Forwarding request to 'systemctl enable supervisord.service'. [root@proxy ~]# service haproxy restart Redirecting to /bin/systemctl restart haproxy.service [root@proxy ~]# service supervisord restart Restarting supervisord (via systemctl): [ OK ] [root@proxy ~]# /opt/proxy/bin/restartServices.sh Redirecting to /bin/systemctl restart haproxy.service Broadcast message from [email protected] (Fri 2019-11-08 14:42:02 UTC): haproxy[3062]: backend vsd has no server available! Message from syslogd@proxy at Nov 8 14:42:02 ... haproxy[3052]:backend vsd has no server available! Restarting supervisord (via systemctl): [ OK ] [root@proxy ~]#
6. Final verification in the nuage proxy.
Below steps, you could perform to verify all the process supposed to work are working correctly.
- First, Lets verify the haproxy.
[root@proxy ~]# ps -ef |grep proxy root 504 1 0 Sep19 ? 00:00:00 /usr/sbin/gssproxy -D root 25620 1 0 10:24 ? 00:00:00 /usr/sbin/haproxy-systemd-wrapper -f /etc/haproxy/haproxy.cfg -p /run/haproxy.pid haproxy 25621 25620 0 10:24 ? 00:00:00 /usr/sbin/haproxy -f /etc/haproxy/haproxy.cfg -p /run/haproxy.pid -Ds root 25661 29018 0 10:24 pts/0 00:00:00 grep --color=auto proxy
- Second, let’s verify the Notification APP.
[root@proxy ~]# ps -ef |grep supervisord root 25649 1 0 10:24 ? 00:00:00 /usr/bin/python /usr/bin/supervisord -c /etc/supervisord.conf root 25663 29018 0 10:24 pts/0 00:00:00 grep --color=auto supervisord [root@proxy ~]#
- Check for any errors in Proxy server
[root@proxy ~]# tail -f /var/log/vns/na.log address: '10.1.5.5', port: 5222 } [26-Sep-2011 06:54:39.791] [LOG] Client reconnects [26-Sep-2011 06:54:39.793] [LOG] Client is connected [26-Sep-2011 06:54:39.801] [LOG] Client reconnects [26-Sep-2011 06:54:39.806] [LOG] Client is connected [26-Sep-2011 06:54:39.883] [LOG] Connected as [email protected]/vsd [26-Sep-2011 06:54:39.883] [LOG] Client is online [26-Sep-2011 06:54:39.889] [LOG] no subscriptions, creating one [26-Sep-2011 06:54:39.893] [LOG] subscribed. sending presence
Nuage utility VM not working?
Sometimes when you complete the installation and trying to bootstrap NSG, then it wouldn’t work. The possible reason because of the Utility VM services hasn’t installed correctly, so you would have to verify all the process are installed correctly by entering the above commands, most of the time either haproxy or notification app would not have started.
Normal error messages.
[root@proxy ~]# tail -f /var/log/vns/na.log [08-Nov-2019 14:43:05.286] [LOG] Client is connected [08-Nov-2019 14:43:05.287] [ERROR] No usable SASL mechanism [08-Nov-2019 14:44:05.300] [LOG] Client is disconnected true undefined [08-Nov-2019 14:44:06.301] [LOG] Client reconnects [08-Nov-2019 14:44:06.303] [LOG] Client is connected [08-Nov-2019 14:44:06.311] [ERROR] No usable SASL mechanism [26-Sep-2011 06:48:24.026] [LOG] Client is disconnected true undefined [26-Sep-2011 06:48:25.028] [LOG] Client reconnects [26-Sep-2011 06:48:25.031] [LOG] Client is connected [26-Sep-2011 06:48:25.032] [ERROR] No usable SASL mechanism [26-Sep-2011 06:49:25.034] [LOG] Client is disconnected true undefined [26-Sep-2011 06:49:26.036] [LOG] Client reconnects [26-Sep-2011 06:49:26.039] [LOG] Client is connected [26-Sep-2011 06:49:26.040] [ERROR] No usable SASL mechanism
This basically means you have not allowed TLS connection via VSD, allowing the TLS would fix this issue. You basically missed one of the step during the VSD installation. Follow in (VSD installation)part 3 under Install VSD services step e.
Let’s go ahead and define the SD-WAN gateway